Can Systems Engineering find a way to counter Violent Radicalization?
Systemic innovation for countering violent radicalization: Systems engineering in a policy context - Clancy - Systems Engineering - Wiley Online Library 2w
Abstract
This paper brings a systems engineering approach to policymaking in the context of violent radicalization. We test strategies to combat terrorism under the premise that violent radicalization is a complex system of social contagion resulting in terrorism.
We built a simulation using DIME-PMESII military standards to replicate a terror contagion occurring over 10 years in both physical and online environments under optimal, realistic, and worst-case scenarios. We then tested antiterrorism, counterterrorism, and counter radicalization strategies as policy experiments in this simulation.
These experiments identified four key dynamics relevant for developing policies to reduce terrorism.
- First, most well-known policies are ineffective in containing terrorism driven by social contagion.
- Second, strategies generating backlash can become worse than doing nothing at all.
- Third, perceived grievance determines the carrying capacity of terrorism in a system, allowing disrupted networks to regenerate.
- Fourth, variable public support may result in sharp secondary waves of violence under certain contingencies.
Experimenting with our model, we explore effective ways to address the violent radicalization problem.
Conclusion
Our goal in this paper was to show how systems engineering can be used in policymaking by conducting simulated experiments into antiterrorism, counterterrorism, and counter radicalization policies for combating terrorism under the premise that violent radicalization operates as a social contagion known as a terror contagion. An important part of this is to show how the analysis of policy life cycles from established methods not commonly applied in systems engineering environments (i.e., system dynamics to evaluate sociotechnical systems and policy life cycles) could be brought into a systems engineering context– using a domain that is ubiquitous in systems engineering literature, defense.
- The first key finding was that terror contagions are driven by positive feedback loops, like a viral infection. The more high-risk population activated to commit acts of terrorism, the larger the number of cultural scripts operating to radicalize others. A system memory, like a viral reservoir, retains cultural scripts conveying violent ideology and methods of mass violence. The reservoir can then reinfect high-risk populations years later. These two factors combine so that once a terror contagion passes a threshold, it gains a high fault tolerance, and years can pass between subsequently completed attacks.
- The second finding was that even when policies are effective in the best case, if they spark backlash effects by being too broadly targeted, they can generate perceived grievance within the high-risk population or the larger population within which the high-risk population exists. This backlash effect can cause a steady increase in the high-risk population, which undermines the policy's effectiveness over time.
- The third finding shows how this perceived grievance is the carrying capacity of the system of a terror contagion serving as both the source of a terror contagion and renewing or restoring violent radicalization networks disrupted by periodic interventions.
- Our fourth finding shows how even a policy that overcomes the previous three challenges can struggle over the long run because as terrorist violence reduces, public perception of risk reduces, and public support for successful intervention declines.
Though early-stage, these experiments in policy research help understand the opportunities and challenges of combatting terror contagions. Future research would advance the simulation from its current form by creating simulations calibrated to specific violent ideologies and corresponding high-risk populations in different geographic regions. Simulation improvements could build upon our existing profiles and data set of 4500 incidents leveraging GTD data.55 Incorporating clustering, hyperdimensional, or machine learning techniques could improve profiles and support calibration.75 Additional calibrations could incorporate natural language processing of social media to identify specific cultural scripts used in a profile.
Finally, within our stated limitations, we note that focused deterrence and terror contagion containment have significant empirical evidentiary support in adjacent domains. Numerous ongoing pilots of focused deterrence show its benefit against criminal gang violence and domestic partner violence. There are several decades of research on countering the Werther effect of celebrity suicide contagion. Although applying these methods to combating terror contagions will require work, it is not starting from scratch. These results should encourage additional research under the premise that violent radicalization is a form of social contagion, either through the terror contagion hypothesis or other alternatives. Developing strategies along this line to counter violent radicalization may open new effective opportunities for reducing terrorist violence.
Summary
Here are the key points from the document:
- Violent radicalization leading to terrorism is a major global security threat. Mass shootings, far-right extremism, and terrorist groups like ISIS are manifestations of this issue.
- Policies to counter violent radicalization fall into three main categories: antiterrorism, counterterrorism, and counter-radicalization. Examples include professional training, threat assessments, gun control laws, community advocacy, and counternarratives.
- Systems engineering and system dynamics modeling can provide a unique perspective on evaluating and improving these policies over their lifecycle. The models examine how policies perform under best case, realistic constraints, and worst case scenarios.
- Key findings from the simulations:
- Popular policies often struggle due to positive feedback loops and cultural scripts acting as a "viral reservoir" to reinfect high-risk populations.
- Policies can backfire if they create grievances that increase the high-risk population over time.
- Perceived grievance is the "carrying capacity" that allows radicalization to renew itself after interventions.
- Successful policies can undermine themselves as reduced terrorism leads to reduced public support.
- Combined policy portfolios like focused deterrence and "terror contagion containment" show promise, but require careful implementation to avoid backlash effects.
- Overall, systems engineering provides a useful approach to evaluating and improving policies to counter violent radicalization and terrorism over time. But more research is needed, especially on regional differences.
Human Irrationality
Based on the information provided in the documents, it does not appear that the simulation model directly accounted for factors like human irrationality, religious beliefs, clan/family ties when modeling violent radicalization. The model takes a high-level perspective focused on population-level dynamics.
However, the model does try to capture some relevant macro-level influences that could reflect these micro-level factors, in an abstract way:
- Perceived grievance - This could encompass irrational yet strongly held grievances rooted in religious, clan or tribal identities.
- Ideological similarity - The tendency for radicals to identify with perpetrators of their same ideology may relate to innate group biases.
- Normal abandonment - Even among radicals, there are innate moral inhibitions against violence that lead some to abandon plans.
- Backlash effects - Aggressive policies may fuel irrational desires for revenge tied to family or group honor.
So while not directly modeled, the structure does try to represent some of the emergent effects of irrational biases, religiosity, family/clan ties on radicalization.
To increase confidence in the model, the researchers could try to incorporate more low-level agents representing varied cognitive, cultural, and social dynamics. Adding and testing these against individual case studies could improve validity. This increased resolution may reveal new insights into how the balance of top-down ideological factors and bottom-up identity factors influence radicalization and policy effectiveness over time.
Verification and Validation
Here is how the researchers verified proper implementation and validated the model against historical data:
Model Verification:
- Used standard system dynamics methods like structure verification and parameter verification
- Checked model structure followed documented causal loop diagrams
- Confirmed parameters were consistent with data sources and literature
- Tested boundary adequacy by evaluating behavior at extremes
- Ran sensitivity analyses to check robustness to parameter changes
- Used unit checking in equations and converted units where necessary
- Peer reviewed model with system dynamics experts
Model Validation:
- Recreated historical growth patterns of terrorist incidents using parameter profiles
- Generated behavior modes (equilibrium, struggle to grow, contagion etc.) that matched real world reference modes
- Checked model could reproduce contagion patterns like Columbine school shootings
- Quantitatively compared simulation output to 4600 real incidents from Global Terrorism Database
- Conducted docking by simulating reduced subsets of model and testing against overall behavior
- Confirmed simulated policies like focused deterrence produced results in line with literature
In summary, they used standard modeling best practices like verification, validation, docking, and sensitivity analysis to ensure the model was properly implemented and consistent with real-world data on terrorism and violence. This provides confidence in using the model to evaluate policies. But the researchers acknowledge the need for continued refinement and validation as new data becomes available.
Policies
the key policies that were tested in the system dynamics simulations include:
Antiterrorism:
- Enhanced law enforcement and bystander response training
- Hardened facilities
- Gun control laws
Counterterrorism:
- Counterterrorism investigations
- Threat assessments
- Red flag laws
Counter-radicalization:
- Community awareness and advocacy
- Efforts to reduce root causes and grievances
Combined policies:
- Focused deterrence (antiterrorism and counterterrorism)
- Terror contagion containment (media guidelines, counter-narratives, highlighting failed attacks)
Some other interventions analyzed:
- Disrupting physical or online radicalization "safe havens"
- Reducing grievances in radicalized populations
- Serial raids/strikes against extremist groups
The simulations tested these policies in isolation and in combined portfolios to evaluate their effectiveness across different scenarios from best case to worst case. The goal was to understand how policies perform over their lifecycle when faced with real-world constraints.
Evaluation Metrics
the key metrics used to evaluate the effectiveness of policies in combating violent radicalization and terrorism were:
- Behavior mode of terrorist incidents over time - Policies were assessed on their ability to shift the behavior mode down to lower levels of terrorism. Going from contagion to struggle to grow to failure to grow and ideally down to equilibrium or below was seen as success.
- Number of contagion incidents - The mean and range of suspected terror contagion incidents were numerically tracked over 1000 simulation permutations. Effective policies reduced the mean number of contagion incidents compared to the baseline.
- Adjusting baseline conditions - Policies were evaluated on their ability to weaken or strengthen the baseline condition they were tested against. For example, shifting from a strong contagion baseline to just a contagion baseline was seen as an improvement.
- Percentage change in contagion incidents - The percent change between the mean number of contagion incidents before and after a policy intervention was calculated. Larger reductions signaled a more effective policy.
- Ability to sustain improvement - Policies were assessed on their ability to sustain improvements over time under realistic constraints like backlash and declining public support. Sudden reversals or subsequent waves of incidents suggested limited sustainability.
- Falsification testing - Policies thought to be effective were falsified by removing components to ensure benefits were arising from hypothesized mechanisms.
The combination of visual behavior modes, numerical metrics, comparisons to baseline conditions, and falsification testing allowed the simulations to rigorously evaluate policies over time under different scenarios.
Simulation and Plans for Future Research:
Simulation Overview:
- System dynamics simulation model representing the lifecycle of violent radicalization and terror contagions
- Models the interactions between incidents, agents, networks, systems of spaces (governed vs ungoverned), and overall system behavior
- Uses stochastic modeling of discrete terror incidents along with underlying differential equations
Key Controllable Parameters:
- Success rates of terror incidents (planning, execution)
- Number of fatalities per incident
- Size of high-risk population
- Perceived grievance levels
- Influence of extremist groups and safe havens
- Strength of policy interventions like deterrence, grievance reduction, contagion containment
Artifacts Generated:
- Timeseries graphs of key variables like number of incidents, fatalities, radicalized population size
- Tables summarizing number of contagion incidents under different scenarios
- Behavior mode diagrams showing changes to overall system behavior over time under policies
Future Research Planned:
- Create simulations calibrated to specific violent ideologies and geographical regions
- Incorporate clustering, machine learning, and natural language processing to improve profiles
- Advance simulation structure based on empirical validation and feedback
- Test combined policy portfolios like focused deterrence and terror contagion containment in field pilots
- Evaluate simulation approach against other methods like agent-based modeling
Overall, the simulation provides a flexible virtual testbed to evaluate policies over their lifecycle under different scenarios. There are many opportunities to advance the artifacts and approach through additional research.
Further Reading and References
SIR Modeling
Introduction
"A brief introduction to the SIR model and what is tells us about the spread of COVID-19.
SIR Model Simply Explained by “Micheal Porter”
The SIR model is one of the most basic models for describing the temporal dynamics of an infectious disease in a population. It compartmentalizes people into one of three categories: those who are Susceptible to the disease, those who are currently Infectious, and those who have Recovered (with immunity). At its most basic level, the SIR model is a set of equations that describes the number (or proportion) of people in each compartment at every point in time. The SIR model is often represented with the following flow diagram that shows the three states (S, I, and R) and arrows depicting the direction of flow between the states.
At this point in the pandemic, you may have seen the usual graphical output from a SIR model that shows the number (or proportion) of people in each state over time
These curves come from the (continuous time) SIR model which specifies a set of three ordinary differential equations:
“As the saying goes,”An equation is worth a thousand words".
Unpacking SIR
Every day a contagious person will randomly move around the population infecting any susceptible person they come into close enough contact with. Let’s say a contagious person will come into close contact with (and cough on, sneeze on, kiss, etc.) an average of (beta) people each day; if those people are susceptible (i.e., not immune) they will become infected otherwise they will just benefit from the close contact. If there are susceptible people on day , the expected number infected by our carrier is , where is the probability a close contact is with a susceptible person.
Our infectious carrier will continue this process of randomly contacting people each day until they are no longer contagious (either by recovery or death). Suppose that every day a contagious person has probability (gamma) of becoming non-contagious. Some readers will recognize that this specifies a geometric distribution for the length of time an infected person is contagious. One property of this model is that the average number of days that someone stays contagious is .
Notice that we have specified two model parameters: and . Because these are greek letters you know they are important! Combined, they make another parameter you may have heard of, the (“R nought”). The , known as the basic reproductive number, is defined as the expected number of people infected from a contagious person over the length of their contagiousness (in a fully susceptible population). If you were paying attention and keeping notes, you may be able to work out that which is the expected number of close contacts per day () multiplied by the average number of days contagious (). If (or equivalently, ), then we will likely have an epidemic on our hands as each infected person will infect more than one other on average, who will infect more than one other, and so on (i.e., exponential growth) until we reach herd immunity (but more on that later).
“But what about those equations?”
Refer back to the SIR ODE equations, they describe the change in counts at an instance of time. We can consider a discrete time version of these equations that describe the changes each day using the concepts described above.
Noten that this will give an approximation of the actual SIR output (and there are better approximations then the one described below). However, don’t let this disrupt your sleep; remember that the SIR model is only an approximation of reality and a discrete time perspective is, in my opinion, a better representation than continuous time (e.g., humans don’t randomly mix for 24 hours each day, data is reported daily, etc). Also keep in mind that the model parameters must be estimated, so the fitted curve for the discrete time version should be similar to the continuous time version (even if the estimated parameter values are slightly different).
For notation, take as the number of Susceptible, Infectious, and Removed people in the population on day . The total population size is assumed to stay constant over the observation period and is equal to the sum of all counts (i.e., ). This discrete time version of the SIR model specifies the equations:
This shows that the three SIR equations describe how the counts in each category change in one day. Consider the change in the number of infectious; it is the sum of two components:
The last line makes clear that this term just multiplies what we described above for a single infectious person by , the total number of infectious people at time . In other words, if one infectious person is expected to infect other people on day , then infectious people are expected to infect on day . Likewise, if each infectious person has probability of recovery or death on day , then the expected total number of infected people that recover (or die) on day is .
We can also examine the first term, corresponding to the number of newly infectious people, with a slightly different formulation
As a reminder, is the transmission parameter and it controls the rate that infectious people can spread the disease (larger values of imply faster spread). The second line makes it explicit that the number of newly infected people at time is proportional to the number of susceptible people at time . Specifically, is referred to as the force of infection and is the fraction of susceptible people who become infectious during time t. Notice that depends on both the transmission parameter and the proportion of people who are infectious at time .
The second term in the equation for the change in infectious people models the number of infectious people that are removed (i.e., recover with immunity or die):
The parameter is the fraction of infectious people that are removed each day. When is large, people will recover (or die) quickly and won’t have as much time to infect the susceptible population. However when is small, people stay infectious longer and have more opportunity to infect others. Because this model is based on expected values, we can consider the separation of into two sub-components to handle deaths and recoveries separately (e.g., ).
If you look back at the SIR equations you’ll notice that the change in susceptibles and removed are based on the two components we just described. That is, the change in susceptibles is minus the number of newly infected and the change in removed is the number of newly recovered. This ensures that total number of people in all bins is always equal to .
For the visually inclined, here is my attempt to represent the flow of counts between times and . The equations above the arrows show the fraction of the counts in the left side bin that get transferred to the right side bin with color indicating if the count is positive (black) or negative (red).
Notice that the flow out of each bin must sum to 1 to preserve the required property that total counts must equal the population size. Look now at the bins on the right side. Because only gets a negative flow it will only decrease (or stay the same) over time. The number of removed at time , only gets positive flow and will only increase (or stay the same) over time. The situation for the number of infectious, is different in that it can increase or decrease over time.
Hopefully this provides you with a little better understanding of the SIR model. It also reveals that the quote is wrong - an equation must be worth more than 1000 words since I have probably reached that limit and still have a few more things to say about herd immunity and .
Make it stop: Herd Immunity and
Let’s concentrate on the number of infectious individuals and write out explicitly the estimate for time :
This shows that , the number of infectious tomorrow, can be expressed as a multiple of the number of infectious today. This leads to the following conditions that determine if the number of infections is increasing, decreasing, or at its peak based on the two model parameters and as well as the proportion of the population that is susceptible .
The peak of the epidemic will occur when the proportion of susceptible people is equal to the ratio
which shows one reason , the “R nought” value mentioned above, is a prominent part of the discussion.
Let’s examine this in more detail. According to the SIR model, the peak of the infection, that is the day when the number of infected people is greatest, is the first day when the proportion of susceptible peoples fall below . Equivalently, this suggests the epidemic will peak when the cumulative proportion of the population that has been infected exceeds . This is what is meant by the term herd immunity - when the fraction of the population that is immune reaches a large enough level that the number infected starts to decline.
A recent post by epidemiologists at Johns Hopkins University suggests that the US is not close to herd immunity. Below is a plot that shows, according to the SIR model, the percentage of a population that needs to be immune before it reaches herd immunity for a given value.
The Johns Hopkins article suggests about 70% of the US needs to be immune to reach herd immunity; this would put . There are all sorts of estimates on for COVID-19, but most that I have seen range between 1.5 and 6.5 (which will of course vary region to region and over time).
Changing the disease dynamics
Now that you know something of the SIR model, it can be insightful to consider how the dynamics change under different strategies. Here are three things a population may consider doing to limit the number of peopled infected with COVID-19
- Reduce the transmission rate (decrease )
- Reduce the length of time that someone is contagious (increase )
- Reduce the number of susceptible people (decrease )
Below is a plot that shows how the infection dynamics are impacted under each strategy. The left facet shows the percentage of the population that is infectious () and the right facet gives the percentage of population that has been infected (). The baseline model uses () in a population of 100,000 people. This implies that each infectious individual will come into contagiously close contact with an average of 0.30 people per day and will stay contagious for an average of 10 days. On day 1, there is a single infectious person leaving susceptible, and recovered. Strategy 1 reduces , Strategy 2 increases (contagious for 8 days on average), and Strategy 3 considers that 10% of the population is immune on day 1 ().
Social distancing policies, limitations on group sizes, and quarantines are used to reduce the transmission rate (decrease ). This action has been taken by most governments around the world to limit the number of people who are infected and results in a “flattening of the curve” as shown by Strategy 1 in the plot. This strategy forces the peak down (and therefore reduces hospital overcrowding), but extends the total outbreak duration. As can be seen from the cumulative plot on the right, it also reduces the total percentage of the population that will be infected.
The second strategy is to reduce the time someone is infectious (increase ). This could be accomplished by medications, supplements, nutrition, exercise, and other treatments. Remdesivir, for example, may reduce the infectious period for up to 4 days on average. In this hypothetical scenario, the SIR model suggests that even a 2 day reduction in the time someone is infectious can have a large impact in the peak number of infections and total number of people infected.
The third strategy is to reduce the susceptible population. This refers to a vaccine, which doesn’t yet exist for COVID-19. According to this SIR model a 10% vaccination rate would not only lead to a reduction in the peak infectious count but also provide the largest reduction in total number of infections (out the three scenarios).
Hopefully, this sheds some light on the different public health responses you have been hearing about in the headlines. There are more variations on the types of mitigation efforts available and certainly better models in which to evaluate how such efforts will impact the disease, but these three strategies and the basic SIR model will take you far in understanding how it all works.
Where to go from here
The purpose of this article is to provide a brief introduction to the SIR model and explain a few of its properties. Hopefully this has cleared up some of the confusion surrounding terms you have been hearing about in the news and also given you a bit more insight into how a compartmental epidemic model works. It may have also left you with other questions and concerns; I’ll outline a few thoughts on where to go next.
The first thing worth mentioning is that the SIR model is undoubtedly wrong in the sense that it doesn’t explain all the complexities and dynamics in the COVID-19 pandemic. But as George Box famously said “All models are wrong, but some are useful”. And the SIR model can be useful in many ways. First, it is a good starting place for understanding the more complex models. Also, never forget that the parameters of these models must be estimated. A simple model can provide better predictions than a more realistic (and complex) model when there is not enough data or the data quality is poor. And we are dealing with both sparsity and quality issues in the COVID-19 data. This is an often under-appreciated aspect of modeling and data analysis.
Nevertheless, I’d say the basic SIR model is too simplistic to be used for accurate modeling of the COVID pandemic. Fortunately, there are several relatively simple ways to improve it. First, we can consider that the transmission parameter (and hence ) can change over time, especially due to social distancing and stay at home regulations. I would be skeptical of any COVID-19 model that didn’t account for changes in the transmission rate, especially with the unprecedented movement restrictions we have seen around the world. Here is a simple analysis that shows how the infectious counts respond if the transmission parameter is abruptly changed during the course of the epidemic.
The baseline scenario is the same as what was considered in Changing the Disease Dynamics section, (). The other scenarios consider that is reduced to on a certain day (e.g., due to a shelter in place order). The top left panel is the baseline scenario. The other panels show how the infectious rate varies if the intervention occurs at different time points in the course of the epidemic. The black line is provided as a reference to the baseline scenario. These plots reveal that early changes in the transmission rate have the strongest effect. A change close to the herd immunity induced peak (bottom right panel) has very little effect.
The basic SIR model is deterministic. This means that once the model parameters ( and ) are specified there is no randomness in the model output. This is apparent by considering that all transitions between compartments are specified by expected values and not probability distributions. One consequence of this is that no uncertainty is represented in the model output - something that can lead to poor decision making. Uncertainty in the model output can be estimated with Monte Carlo simulation of a stochastic SIR model. In a stochastic SIR, instead of modeling exactly newly infectious on day , the number of newly infectious is randomly determined according to a Binomial distribution (). Likewise, the number of infectious people that recover is no longer exactly , but randomly determined according to the Binomial distribution (). The stochastic SIR will produce a different set of curves every time it is simulated. To get a sense of the uncertainty, the stochastic SIR can be simulated 100’s or 1000’s of times. For example, below is the result of running a stochastic version of the SIR model 100 times.
Notice that while the peak number of infectious is very consistent (around 31.2K), the timing of the peak has much greater variability, starting as early as day 58 in one simulation and including one simulation that doesn’t reach the peak until day 93. A word of caution: the stochastic SIR only addresses the uncertainty in the model output, but doesn’t address the uncertainty in estimating the model parameters (i.e., it assumes and are known exactly). Parameter uncertainty, especially early in the outbreak when data is limited, will have an even greater influence on how precisely we can make predictions. Making decisions under uncertainty is the rule rather than the exception for this pandemic!
There are many other compartmental models that extend SIR. The closest is the SEIR model that splits out the infected population into two sub-groups, those who are infected but not yet contagious and those who are infectious. The SEIR model is very similar to the SIR model, but Susceptible people who become infected move first move into the Exposed group. There is one additional parameter that controls how long a person stays in the Exposed group before they move into the Infectious state.
The basic framework can be extended to include more detailed compartments and transitions, like having separate parameters for different age groups or how likely people from different geographic locations will interact, etc. For very complex model specifications, Agent-Based Models (ABM) can be employed to understand the corresponding disease dynamics. You can think of an ABM as a type of stochastic compartmental model on steroids; it can capture very complex population behavior using agents that follow relatively simple rules (e.g., leave home between 8-9am, go to work, stop for groceries once per week, go out to eat 2 times per week) and can have individual disease progression (e.g., an older agent has higher probability of becoming hospitalized).
I’ll close this article with mention of an all together different way to estimate epi-curves is with a pattern-based or curve fitting approach. This is the approach taken by Institute for Health Metrics and Evaluation and is based on the observation that over a wide range of parameter values, the SIR/SEIR models maintain a similar shape. For example, notice from the plots above that the curves representing the number/percentage of infectious people look rather bell-shaped. For those of you who have taken a Statistics course, the mention of “bell-shaped” will evoke the wonderful memories of the Central Limit Theorem and the Gaussian or Normal distribution. The IHME modelers exploit this observation and directly estimate the parameters of a Gaussian shaped epi-curve. This approach offers a different way to estimate model parameters (e.g., using fatality data) with a focus on forecasting.
Giovanni Valentini (2024). SIR Epidemic Spread Model (https://www.mathworks.com/matlabcentral/fileexchange/75100-sir-epidemic-spread-model), MATLAB Central File Exchange. Retrieved .
The SIR Model for Spread of Disease - The Differential Equation Model
As the first step in the modeling process, we identify the independent and dependent variables. The independent variable is time t, measured in days. We consider two related sets of dependent variables.
The first set of dependent variables counts people in each of the groups, each as a function of time:
| S = S(t) | is the number of susceptible individuals, |
| I = I(t) | is the number of infected individuals, and |
| R = R(t) | is the number of recovered individuals. |
The second set of dependent variables represents the fraction of the total population in each of the three categories. So, if N is the total population (7,900,000 in our example), we have
| s(t) = S(t)/N, | the susceptible fraction of the population, |
| i(t) = I(t)/N, | the infected fraction of the population, and |
| r(t) = R(t)/N, | the recovered fraction of the population. |
It may seem more natural to work with population counts, but some of our calculations will be simpler if we use the fractions instead. The two sets of dependent variables are proportional to each other, so either set will give us the same information about the progress of the epidemic.
- Under the assumptions we have made, how do you think s(t) should vary with time? How should r(t) vary with time? How should i(t) vary with time?
- Sketch on a piece of paper what you think the graph of each of these functions looks like.
- Explain why, at each time t, s(t) + i(t) + r(t) = 1.
Next we make some assumptions about the rates of change of our dependent variables:
-
No one is added to the susceptible group, since we are ignoring births and immigration. The only way an individual leaves the susceptible group is by becoming infected. We assume that the time-rate of change of S(t), the number of susceptibles,1 depends on the number already susceptible, the number of individuals already infected, and the amount of contact between susceptibles and infecteds. In particular, suppose that each infected individual has a fixed number b of contacts per day that are sufficient to spread the disease. Not all these contacts are with susceptible individuals. If we assume a homogeneous mixing of the population, the fraction of these contacts that are with susceptibles is s(t). Thus, on average, each infected individual generates b s(t) new infected individuals per day. [With a large susceptible population and a relatively small infected population, we can ignore tricky counting situations such as a single susceptible encountering more than one infected in a given day.]
- We also assume that a fixed fraction k of the infected group will recover during any given day. For example, if the average duration of infection is three days, then, on average, one-third of the currently infected population recovers each day. (Strictly speaking, what we mean by "infected" is really "infectious," that is, capable of spreading the disease to a susceptible person. A "recovered" person can still feel miserable, and might even die later from pneumonia.)
Let's see what these assumptions tell us about derivatives of our dependent variables.
- The Susceptible Equation. Explain carefully how each component of the differential equation

(1)
follows from the text preceding this step. In particular,- Why is the factor of I(t) present?
- Where did the negative sign come from?

(2) - The Recovered Equation. Explain how the corresponding differential equation for r(t),

(3)
follows from one of the assumptions preceding Step 4. - The Infected Equation. Explain why

(4)
What assumption about the model does this reflect? Now explain carefully how each component of the equation
(5)
follows from what you have done thus far. In particular,- Why are there two terms?
- Why is it reasonable that the rate of flow from the infected population to the recovered population should depend only on i(t) ?
- Where did the minus sign come from?
Finally, we complete our model by giving each differential equation an initial condition. For this particular virus -- Hong Kong flu in New York City in the late 1960's -- hardly anyone was immune at the beginning of the epidemic, so almost everyone was susceptible. We will assume that there was a trace level of infection in the population, say, 10 people.2 Thus, our initial values for the population variables are
| S(0) = 7,900,000 |
| I(0) = 10 |
| R(0) = 0 |
In terms of the scaled variables, these initial conditions are
| s(0) = 1 |
| i(0) = 1.27 x 10- 6 |
| r(0) = 0 |
(Note: The sum of our starting populations is not exactly N, nor is the sum of our fractions exactly 1. The trace level of infection is so small that this won't make any difference.) Our complete model is
 |
(6) |
We don't know values for the parameters b and k yet, but we can estimate them, and then adjust them as necessary to fit the excess death data. We have already estimated the average period of infectiousness at three days, so that would suggest k = 1/3. If we guess that each infected would make a possibly infecting contact every two days, then b would be 1/2. We emphasize that this is just a guess. The following plot shows the solution curves for these choices of b and k.

- In steps 1 and 2, you
recorded your ideas about what the solution functions should look like.
How do those ideas compare with the figure above? In particular,
- What do you think about the relatively low level of infection at the peak of the epidemic?
- Can you see how a low peak level of infection can nevertheless lead to more than half the population getting sick? Explain.
In Part 3, we will see how solution curves can be computed even without formulas for the solution functions.
1 Note that we have turned the adjective "susceptible" into a noun. It is common usage in epidemiology to refer to "susceptibles," "infecteds," and "recovereds" rather than always use longer phrases such as "population of susceptible people" or even "the susceptible group."
2 While I(0) is normally small relative to N, we must have I(0) > 0 for an epidemic to develop. Equation (5) says, quite reasonably, that if I = 0 at time 0 (or any time), then dI/dt = 0 as well, and there can never be any increase from the 0 level of infection.
David Smith and Lang Moore, "The SIR Model for Spread of Disease - The Differential Equation Model," Convergence (December 2004)
Counter-Terrorism Module 2 Key Issues:
Radicalization & Violent Extremism
This module is a resource for lecturers
As with the concept of 'terrorism', there is no universally agreed definition of the term 'violent extremism'; indeed, somewhat confusingly, the terms can sometimes be employed interchangeably. There are, however, a number of definitions which have been developed at the national, regional and international levels. A recent United Nations High Commissioner for Human Rights (UNHCHR) Report on good practices and lessons learned on how protecting and promoting human rights contribute to preventing and countering violent extremism examined existing State practice on policies and measures governing 'violent extremism' (General Assembly, Human Rights Council report A/HRC/33/29). This revealed very diverse national approaches (para. 17), a number of which are included in the 'interest box' below. The challenges associated with defining the phenomenon are also revealed in the Report's finding that "[i]n other cases, definitions employed do not make fully clear whether 'violent extremism' presupposes violent action or inciting violent action, or whether lesser forms of conduct that do not normally trigger criminal law sanctions would also be included." (Para. 17). Generally, the diversity of definitional approaches reveals some consistency in that the phenomenon of 'violent extremism' is regarded as being broader than that of terrorism. This is also reflected in the VE Action Plan in which the Secretary-General observed that "violent extremism encompasses a wider category of manifestations" than terrorism since it includes forms of ideologically motivated violence that falls short of constituting terrorist acts (General Assembly report A/70/674, para. 4).
The diversity of what may constitute 'violent extremism' has, to some extent, been shaped by the activities of terrorist groups such as Islamic State of Iraq and the Levant (ISIL), Al Qaeda and Boko Haram, which spread messages of hate and violence as well as religious, cultural and social intolerance. In doing so, groups engaged in violent extremism often distort and exploit religious beliefs, ethnic differences and political ideologies to legitimize their actions as well as to recruit and retain their followers.
Potential pitfalls, that some PVE/CVE efforts have become casualties of, include oversimplification of the phenomenon inter alia with respect to its association with any specific religion, nationality, civilization or ethnic group which can have the effect of furthering rather than hindering violent extremism agendas. For instance, the United States of America's Department of State, in its 2016 Strategy on Countering Violent Extremism, recognized this diversity where itnoted that "the drivers of violent extremism vary across individuals, communities, and regions" (US Department of State and USAID, 2016, p. 3). Despite the focus being on returning foreign terrorist fighters, the understanding of the United States resonates with the contents of The Hague-Marrakech Memorandum, where it was recognized that there is a need for a move towards an individual approach to PVE/CVE efforts. For instance, at Good Practices 16 and 19, the Memorandum suggested that States should deploy individual risk assessment tools, that consider a variety of factors, with the assessments being overseen by trained professionals (GCTF, (A), p. 8). This was reinforced in the addendum to the Memorandum, which recommended for the individual risk assessment tool to be implemented by an expert "proficient in understanding the many facets of radicalisation and the local and cultural context" (GCTF, (B), p. 4).
One aspect that States as well as commentators have sometimes oversimplified is the notion of 'radicalization', a concept which has attracted much attention (and related controversies) including in relation to counter-terrorism prevention discourse and efforts. The UNHCHR Report observed that:
The notion of 'radicalization' is generally used [by some States] to convey the idea of a process through which an individual adopts an increasingly extremist set of beliefs and aspirations. This may include, but is not defined by, the willingness to condone, support, facilitate or use violence to further political, ideological, religious or other goals. (Report A/HRC/33/29, para. 19).
Some commentators have suggested that 'radicalization' can be understood as the process by which individuals adopt violent extremist ideologies that may lead them to commit terrorist acts, or which are likely to render them more vulnerable to recruitment by terrorist organizations (Romaniuk, 2015, pp. 7-8).
Recruitment patterns
Recruitment can take many different approaches. Here is one set of proposed models as to how these might be categorized and critiqued:*
- 'The Net': violent extremist and terrorist groups disseminate undifferentiated propaganda, such as video clips or messages, to a target population deemed homogeneous and receptive to the propaganda.
- 'The funnel': entails an incremental approach, to target specific individuals considered ready for recruitment, using psychological techniques to increase commitment and dedication. Even targeted children who resist complete recruitment may develop positive outlooks on the group's activities.
- 'Infection': when the target population is difficult to reach, an 'agent' can be inserted to pursue recruitment from within, employing direct and personal appeals. The social bonds between the recruiter and the targets may be strengthened by appealing to grievances, such as marginalization or social frustration.
* Gerwehr, Scott, and Sara A. Daly (2006). Al-Qaida: terrorist selection and recruitment. Santa Monica, California, RAND Corporation. Pp. 76-80. Cited in United Nations, UNODC (2017). Handbook on Children Recruited and Exploited by Terrorist and Violent Extremist Groups: Role of the Justice System . Vienna. P. 13.
As many commentators and governmental/intergovernmental entities now recognize, historically too much emphasis was given to religio-centric ideology as a driver of terrorism (Kundnani, 2015, pp. 10-11), often at the expense of other critical underlying factors being overlooked or given inadequate attention. At the heart of the movement critical of this limited approach is the work of Botha, who drew attention to the significance of individual psychology as being an essential component in the turn to extremism (including terrorism), with Botha concluding that in order to further prevent terrorism it is essential that improved understanding is developed as to what motivates an individual to turn to terrorism (Botha, 2015, p. 3). For example, one of the key findings of the United Nations Development Programme (UNDP) report, Journey to Extremism in Africa (UNDP Report) (2017), was that while 51% of people interviewed cited religious grounds as a reason for joining violent extremist groups, as many as 57 percent of the respondents also admitted to limited or no understanding of religious texts.
The previously mentioned study conducted by Botha supplements this, as it was determined that far from religion being a key component in radicalization, one of the strongest influences was that of an individual losing faith in politicians and political systems. Critically, Botha's study revealed that anger was commonly targeted at agents of the State, due to their role in protecting the incumbent; the impact of this can be seen when the following is considered: "instead of preventing and combating terrorism [the repressive approaches of agents of the State] ensure that young people affected by them - and even other family members - [were] radicalised" (Botha, 2015, p. 13). Certainly, there has been increased recognition that an over emphasis on radicalization may lead to overly simplistic conclusions regarding the causal links between radicalization (resulting in extremist thoughts) and acts of violent extremism. This may invite a 'deprogramming' approach as a/the solution in response without adequately examining other pathways to violence such as socio-economic factors, discussed in the next section. Certainly, the benefit of increased understanding and lessons learnt are reflected in the approach of the VE Action Plan around which the analysis in this Module has been framed.
It is interesting to note that, at times, academic scholarship has been ahead of governmental and intergovernmental institutions in terms of its understanding and thinking on PVE/CVE related issues. For example, Martha Crenshaw, writing back in 1988, noted that the "actions of terrorist organisations are based on a subjective interpretation of the world rather than objective reality", with Crenshaw arguing that the perception of the political and social environment is filtered through their own beliefs and attitudes (Crenshaw, 1988, p. 2). Nowadays, there is increased understanding that the process of radicalization is highly individualized, with no single pathway and often taking many different forms (General Assembly, Human Rights Council report A/HRC/31/65, para. 15). Scholars have drawn on the social-psychological distinctions within beliefs, feelings, and behaviours to disaggregate the radicalization process. Those who turn to terrorist action only form the apex of a pyramid of a larger group of sympathizers who share their beliefs and feelings (McCauley and Moskalenko, 2008; General Assembly report A/70/674, para. 32).
In examining drivers of violent extremism, great caution must be exercised in the terminology used in order to avoid being misinformed by incorrect and/or unchallenged related assumptions. Consequently, some entities have reviewed their definitional and conceptual approaches, such as the European Police Office (Europol) which recently proposed a move away from the term "radicalization" to "violent extremist social trend" (EUROPOL, 2016).
One significant issue, which must be clarified from the outset, is that what is critical to counter-terrorism discourse and efforts is not per se whether individuals hold 'radical' or 'extremist' views (terms which can be relatively subjective in nature and therefore susceptible to misunderstanding) but whether such views are translated into violent acts (which is the exception rather than the norm). Potentially, millions of people drawn from different social, ethnic, cultural, religious, or geographical backgrounds have what some others might regard as 'radical' or 'extremist' views, especially when compared with their own ones, yet do not commit violent or terrorist acts. Indeed, even how the terms 'violent' and 'violent extremism' are defined can vary contextually depending on the method and methodologies used. For instance, a positivist understanding of 'violent extremism' would differ from one derived from the application of a method of 'micro-narratives' or collecting life stories. Micro-narratives are undoubtedly important for better comprehending or addressing more local drivers of violent extremism.
Definitional approaches to 'violent extremism'
There are many different governmental and intergovernmental definitional approaches to the concept of violent extremism, some examples of which are given here.
Governmental
Australia (1*): "Violent extremism is the beliefs and actions of people who support or use violence to achieve ideological, religious or political goals. This includes terrorism and other forms of politically motivated and communal violence."
Canada (2**): "[V]iolent extremism" is where an offence is "primarily motivated by extreme political, religious or ideological views". Some definitions explicitly note that radical views are by no means a problem in themselves, but that they become a threat to national security when such views are put into violent action
USA (3*): The FBI defines violent extremism as the "encouraging, condoning, justifying, or supporting the commission of a violent act to achieve political, ideological, religious, social, or economic goals", whilst USAID defines violent extremist activities as the "advocating, engaging in, preparing, or otherwise supporting ideologically motivated or justified violence to further social, economic or political objectives".
Norway (4*): Violent extremism constitutes activities of persons and groups that are willing to use violence in order to achieve political, ideological or religious goals.
Sweden (5*): A violent extremist is someone "deemed repeatedly to have displayed behaviour that does not just accept the use of violence but also supports or exercises ideologically motivated violence to promote something".
UK (6*): Extremism is defined as the vocal or active opposition to fundamental values, including democracy, the rule of law, individual liberty and the mutual respect and tolerance of different faiths and beliefs, as well as calls for the death of United Kingdom armed forces at home or abroad.
Intergovernmental
Organization for Economic Cooperation and Development (OECD) (7*): "[P]romoting views which foment and incite violence in furtherance of particular beliefs, and foster hatred which might lead to inter-community violence".
United Nations Educational, Scientific and Cultural Organisation (UNESCO) (8*): Whilst recognizing that there is no internationally agreed-upon definition, UNESCO, within the Preventing violent extremism through education: a guide for policy-makers document, suggested that the most common understanding of the term, and the one which it follows within the guide, is one that "refers to the beliefs and actions of people who support or use violence to achieve ideological, religious or political goals". This can include "terrorism and other forms of politically motivated violence".
1* Parliament of Australia (2015). " Australian Government measures to counter violent extremism: a quick guide." February.
2* Public Safety Canada (2009). " Assessing the Risk of Violent Extremists." Research Summary, vol. 14, no. 4.
3* USAID (2011). " The Development Response to Violent Extremism and Insurgency: Putting Principles Into Practice." USAID Policy, September 2011. P. 2.
4* Norwegian Ministry of Justice and Public Security (2014). " Action Plan Against Radicalization and Violent Extremism." P.7.
5* Government Offices of Sweden (2011). " Sweden Action Plan to Safeguard Democracy Against Violence Promoting Extremism." Government Communication 2011/12:44, Point 3.2.
6* HM Government (UK) (2015). Counter-Extremism Strategy . London, Counter-Extremism Directorate, Home Office. Para. 1. See too HM Government (2011). Prevent Strategy . The Stationery Office, Norwich. Annex A. Note that the 2013 UK Task Force on Tackling Radicalisation and Extremism defined "Islamist extremism".
7* Organization for Economic Cooperation and Development (OECD), Development Assistance Committee (2016). DAC High Level Meeting, Communiqué of 19 February 2016 .
8* United Nations, UNESCO (2017). Preventing violent extremism through education: A guide for policy-makers . Paris, France.
 Next page
Next page
 Back to top
Back to top
Radicalization and Violent Extremism:
Risk Factors, Causes and Threat Assessment Workshop at UCSB
The focus of the workshop is on identifying risk factors, causes and drivers of radicalization, including the role of self-uncertainty, small group dynamics, personality profiles, criminogenic factors, mental health issues as well as social-ecological characteristics of the surrounding environment. At the same time the workshop seeks to address the question of how empirical evidence on risk factors and causes of radicalization should/are informing threat assessment tools and policies of prevention and interdiction in the area of countering violent extremism. The workshop explores these questions in the context of all forms of violent extremism; lone actors and group-based; religious and politically motivated; domestic and foreign fighting. Core issues to be addressed include:
- Conversion, group new-comers and status seeking
- Interaction between personality and self-uncertainty in radicalization
- Appropriateness of existing risk assessment tools of violent extremism
- Overlap between criminal and extremist milieus – the uniqueness of risk factors of violent extremism
- Neighborhood effects on the emergence of radical groups in some localities rather than others
- Enclave deliberation, group polarization and self-uncertainty reduction
- Effectiveness of civic engagement encouragement and other principles in counter-radicalization work
- Systematic differences/similarities between various forms of radicalization and violent extremism
The purpose of the workshop is to bring together leading scholars in the area of terrorism and security studies, the psychology and social psychology of extremist violence and political aggression, criminology and sociology of violence for an inter-disciplinary exchange of views on empirical research findings, their implications for threat assessment and policies and future research projects and ideas. The format of the workshop will be a mix of presentations and plenary discussions in a relatively small setting of invited participants (about 15).
Presenter Biographies and Abstracts
Martha Crenshaw “What is new about “radicalization”?”
Interest in the individual level of terrorism or “violent extremism” is longstanding. Many studies have investigated the question of why a small number of people who have had similar experiences and been exposed to the same ideologies turn to violence in the service of a political cause. What has changed since researchers began analyzing the subject in the 1970s and 1980s? Human psychology at the individual and group levels remains constant.
- What has changed is likely to be the environment. The first critical transformation concerns what can be called permissive conditions. Here the rise of social media in particular as well as advances in communications technology in general have increased the velocity and the worldwide scope of “radicalization” processes.
- More problematic is the second question of possible change in the instigating or motivating factors for an individual’s turn to violence. Is there a fundamental difference between contemporary radical Islamist/jihadist ideologies and historical predecessors such as revolutionary socialism or nationalism?
Lasse Lindekilde “British Muslims Mobilization against Islamist Extremism: The Importance of Action Appeals and Trust”
Research on social movements and collective action has most often been silent on the issue of the effect of characteristics of the mobilizer on the success or failure of mobilization. Most studies in these fields investigate either successful cases of mobilization or collect data on intended behaviours without specifying to respondents, who it is that makes the appeal for action. This paper takes a first step in providing answers to the question of whether and how characteristics of the mobilizer matter to the success of mobilization. It does so by testing hypotheses derived from the literature on persuasive communication and related research, on the case of British Muslims‘ collective action against Islamist extremism.
The data come from a survey experiment of British Muslims (n=825). It features a short scenario about a terrorist attack perpetrated by British Muslim attackers and a subsequent call to action by three different mobilizers (conditions): the British Government, the Muslim Council of Britain (MCB) or nobody specific. We investigate to what degree it matters for British Muslims‘ willingness to engage in collective action, who calls upon them to stand up against Islamist extremism. In doing so we also take into account other relevant variables, including trust in Government/MCB, group efficacy, protest experience, issue saliance, ideological attitudes, identity strength, and emotions.
Lella Nouri "‘Fit into our community or piss off back to the prehistoric shithole you came from’: Threat-based boundaries and social-media political community building by the Far Right.”
On 14th March 2018, Facebook banned Britain First from its platform, reasoning that they had “repeatedly posted content designed to incite animosity and hatred against minority groups” (Guardian, 2018). This came just a week after Britain First Leader Paul Golding and Deputy Leader Jayda Fransen were collectively convicted of four counts of hate crime and jailed for a combined period of 54 weeks. The removal of Britain First from Facebook has sparked debate about the content of the group’s Facebook page and its posts, with high-profile figures such as the Mayor of London, Sadiq Khan, describing the group as “a vile and hate-fuelled group whose sole purpose is to sow division” (The New York Times, 2018). By this time last year, Britain First had succeeded in receiving over 1.9 million likes and attracting 1.6 million followers on Facebook (Nouri, Lorenzo-Dus and Di-Cristofaro, 2017), thus making it by far the most popular political party on the platform. Since then these numbers increased still further, with over 2 million likes and 1.8 million followers, meaning that until its removal Britain First had the “second most liked Facebook page in the politics and society category in the UK – after the royal family” (Hope not Hate, 2018).
Against this backdrop, an important question emerges, why does use of social media by groups like Britain First result in such unprecedented popularity? By examining comparative data collected from Facebook and Twitter on two groups that can be classified under the far-right umbrella: Britain First and Reclaim Australia.
The main aim of our paper is to examine how they use social media. This is crucial for reaching a nuanced understanding of causation in radicalisation processes since ‘how things happen is why they happen’ (Tilly 2006, 410). Drawing upon a +4million word corpus comprising all the Facebook and Twitter posts by Britain First and Reclaim Australia between 21st January and 11th April 2017, our paper examines the linguistic strategies used by both groups.
Our analysis reveals that the overriding goal of these far-right groups’ use of social media is to establish an ‘imagined political community’ (Anderson,1991). Crucially, the relative salience and inter-relations between the constitutive features of these groups’ communities differ significantly from those proposed by Anderson. Most noticeably, establishing threats against boundaries – rather than developing national narratives – emerges as the main pillar on which these groups’ imagined communities rest. Our analysis also reveals that threat-based boundary establishment is primarily realised by these groups through discursive practices of othering (Coupland 2010), which are known to have an influential effect in digital terrorist propaganda (Lorenzo-Dus & Macdonald 2018).
By providing, to our knowledge, the first systematic study of Britain First and Reclaim Australia’s social media discourse, our paper advances understanding of how the far right uses social media and why their use proves so popular. Additionally, and by empirically testing theories of political group formation (specifically, Anderson’s seminal work) on these groups’ use of social media, our paper puts forward a new model of imagined political community for the far right – one that we hope may be further tested and applied to other extremist groups and media platforms.
Mikkel Hjelt “The ’Where’ of Radicalization: The Social Ecology of Radicalization in Denmark”
My presentation focuses on the connection between individuals and their immediate surroundings in producing radicalization. Therefore, I investigate the immediate socio-physical or virtual environment by characterizing the functions of the radical settings, understanding the individual’s exposure to radical settings, and explaining what characterizes neighborhoods in which radical settings emerge. The data collection has been carried out in Aarhus, Denmark, wherefrom several foreign fighters have left for Syria and Iraq. The data collection applies a mixed methods approach, combining one-on-one interviews and focus groups.
Criminology constitutes the core theoretical framework of the project, more specifically, Situational Action Theory. Furthermore, the project draws on more specific theories of radicalization and extremism. My empirical findings underline the importance of the contextual level in understanding radicalization.
- First, exposure to radical settings begins early through a combination of social selection, networks, and recruitment since these young people live close to each other, attend the same schools, or participate in the same leisure activities.
- Second, these radical milieus are settings where you connect with other likeminded, socialize and develop a certain common identity through various activities, and discuss religious and political relations and actions, for example, leaving for Syria and Iraq. These radical settings intertwine a physical and virtual companionship.
- Third, the radical settings center on locations such as mosques or apartments in certain neighborhoods in Aarhus.
- Fourth, the broader socio-physical context seems to affect the emergence of radical settings. The neighborhood of my field research is, on the one hand, a community with a strong sense of mutual trust, helping, looking out for, and knowing each other.
On the other hand, the same positive neighborhood characteristics also have a downside. These aspects of social organization, collective efficacy, and social capital seem to be limited internally. In this sense, the area is partly detached from the broader society. Furthermore, this neighborhood encapsulates a certain moral context that promotes certain norms, values, and feelings of identity, some of which may be conducive to radicalization.
Michael Hogg “Identity Uncertainty and the Social Psychology of Radicalization”
According to uncertainty-identity theory (e.g., Hogg, 2012), a key motivation associated with group identification and group and intergroup behaviors is reduction of self/identity related uncertainty. Because this motivation is more effectively satisfied by highly entitative groups that provide a distinctive and clear identity, people can develop a social identity preference under uncertainty for xenophobic groups that are intolerant of internal dissent and have autocratic leaders (e.g., Hogg, 2014). Uncertainty identity theory research has shown:
- (1) self-related uncertainty strengthens group identification,
- (2) particularly with distinctive groups that have a clearly defined and unambiguous identity;
- (3) in the absence of an available socially valued identity uncertainty can motivate identification with societally devalued groups;
- (4) uncertainty motivates people to accentuate the distinctiveness of a group they belong to and of its identity, and
- (5) can cause people to dis-identify with groups that do not have a distinctive identity;
- (6) uncertainty motives a need for leadership,
- (7) particularly leadership that delivers an unambiguous identity message in an affirmational and directive/autocratic style that is uncertainty reducing;
- (8) uncertainty can also create a preference for leaders who possess the Dark Triad traits of Machiavellianism, narcissism and psychopathy, and can facilitate such people’s successfully attainment of leadership; and
- (9) people who are uncertain about their membership status in a group that matters to them are the most likely to become zealots who engage in extreme intergroup behavior on behalf of the group.
In this talk I overview uncertainty identity theory and its findings in order to underscore the potentially powerful role that identity uncertainty plays in radicalization and violent extremism.
Oluf Gøtzsche-Astrup “Resorting to violence: A generalized dark mindset mediates the effect of uncertainty on intentions to engage in political violence”
I present and test a theoretical framework that explains how fundamental uncertainty can lead to acts of political violence at the individual level. Existing theories claim that fundamental uncertainty is central to predicting political violence, but there is debate concerning the mechanism through which this happens.
Drawing on social identity theory and cognitive and behavioral neuroscience, I argue that the negative emotionality caused by fundamental uncertainty is attributed to broader causes in the world through cognitive biases, which causes the individual to hold a dark mindset of the world. This dark mindset in turn makes acts of political violence, but not legal activism, seem necessary and attractive as an ingroup defense.
In an observational pilot study and a population representative concurrent double randomization design study in the United States and Denmark, the mechanism linking fundamental uncertainty to political violence is tested. The results support the theoretical model and indicate a new target for policy interventions that attempt to lessen political violence caused by economic and political instability in society.
Clark McCauley “Evolution of the Psychology of Terrorism: Lessons for Analysts and Security Officials”
Looking back over developments in the psychology of radicalization and terrorism, several trends emerge. First was a turn away from seeing terrorists as crazy to seeing them in a rational choice framework in which at least terrorist leaders try to maximize the effectiveness of strategies and tactics. A more recent development gives greater attention to emotions in explaining terrorist behavior. Second, and related to the first, there was initially an emphasis on individual-level explanations of terrorism, then a recognition of the power of group, and most recently increased attention to the social movement and public opinion contexts in which terrorism occurs. Third, initial efforts to understand terrorism focused on them—the terrorists. Building now, if slowly, is attention to the action-and-reaction dynamic of the conflict between terrorists and the government they oppose. Several implications of recent trends are briefly identified.
David Parker “Encouraging Public Reporting of Radicalisation: The Impact of Framing”
Anecdotal and qualitative research suggests that when encouraging the public to report concerns of radicalisation, framing this action in terms of safeguarding the individual in question (i.e. a care framing) is the most effective.
This approach is employed in a range of countries, including the UK and Denmark. Despite this, data available indicates that of all referrals received, the proportion from the public is extremely low. Furthermore, communication efforts to date have prioritised specific communities rather than the general population. However, anecdotal information indicates the potential for future radicalisation awareness communications to fall under broader CT branding that prioritises a risk framing. Such an approach would be in line with research that suggests risk framing can be an effective approach in influencing public opinion / behaviour.
This presentation discusses the use of an experimental survey with an N-set of 4,000 nationally representative members of the public (2,000 in the UK and 2,000 in Denmark). The survey experiment seeks to identify causal inference on behavioural intentions when communications prioritise a risk or care framing (using intimacy as a further treatment) and attitudes towards the behaviour that could act as barriers of drivers of reporting. This data will add to the academic literature on both framing and counter radicalisation as well as having significant policy relevance for a range of states delivering radicalisation prevention strategies.
Noemié Bouhana “Nothing More Practical Than a Good Theory: Development of a Causal Meta-Framework to Support the Assessment of Radicalisation and Terrorism Risk”
Changes in terrorist patterns over time and the unreliability of risk factors and indicators reflected in the absence of empirically-supported, stable terrorist profiles have hampered efforts to develop structured tools in support of frontline risk assessment of individual radicalisation and terrorism. As low base rates remain an insurmountable obstacle to the adoption of actuarial methods, structured professional judgement has emerged as the approach of choice for use in preventative, investigative and prison settings. This begs the question, however, of how such a judgement should be structured.
This paper presents work carried out to develop a risk analysis, causally-informed meta-framework grounded in criminological theory (specifically, Situational Action Theory and opportunity theories) to support risk assessment practice above and beyond the use of risk factor-based tools. Findings from the EU-funded FP7 PRIME project on lone actor extremism, which draw from a dataset of 125 offenders, and from a qualitative study of radicalisation carried out in UK high-security prisons, are used to illustrate the conceptual necessity and the practical, diagnostic value of the proposed framework.
Amy-Louise Watkin and Seán Looney “‘The Lions of Tomorrow’ A News Value Analysis of Child Images in Jihadi Magazines”
This paper reports and discusses the results of a study that investigated photographic images of children in five online terrorist magazines to understand the roles of children in these groups. The analysis encompasses issues from 2009-2016 of
- Inspire,
- Dabiq,
- Jihad Recollections (JR),
- Azan and
- Gaidi Mtanni (GM) .
The total number of images was 94. A news value framework was applied which systematically investigated what values the images held that resulted in them being ‘newsworthy’ enough to be published.
This paper discusses the key findings which were that Dabiq distinguished different roles for boys and girls, portrayed fierce and prestigious boy child perpetrators, and children flourishing under the caliphate. It is thought that these images intended to inspire sympathisers to join and were a form of psychological warfare. Inspire and Azan focused on portraying children as victims of Western-backed warfare which is thought to have been an attempt to create feelings of guilt and anger towards the West. Finally, GM portrayed children supporting the cause peacefully, and JM contained no re-occurring findings. This is thought to be because the groups believed that using children would portray them negatively.
Terrorism and the internet: How dangerous is online radicalization?
ncbi.nlm.nih.gov- Journal List
- Front Psychol
- PMC9606324
Articles from Frontiers in Psychology are provided here courtesy of Frontiers Media SA
Extremist ideology as a complex contagion: the spread of far-right radicalization in the United States between 2005 and 2017
Introduction
The far-right movement, which includes white supremacists, neo-Nazis, and sovereign citizens, is the oldest and most deadly form of domestic extremism in the United States (Piazza, 2017; Simi and Bubolz, 2017). Despite some ideological diversity, members of the far-right often advocate for the use of violence to bring about an “idealized future favoring a particular group, whether this group identity is racial, pseudo-national, or characterized by individualistic traits” (National Consortium for the Study of Terrorism and Responses to Terrorism (START), University of Maryland, 2017). Over the last decade, the far-right movement was responsible for 73.3% of all extremist murders in the United States. In 2018, this statistic rose to 98% (The Anti-Defamation League Center on Extremism, 2019). The increasing severity of far-right extremist violence, as well as the associated rhetoric on social media (Davey and Ebner, 2019; Winter, 2019), has generated public concern about the spread of radicalization in the United States. Former extremists have referred to it as a public health issue (Allam, 2019; Bonn, 2019), an idea advocated for by some policy experts as well (Sanir et al., 2017; Weine and Eisenman, 2016).
There is little evidence that radicalization is primarily driven by psychopathology (Misiak et al., 2019; Post, 2015; Webber and Kruglanski, 2017). Rather, radicalization appears to be a process in which individuals are destabilized by various environmental factors, exposed to extremist ideology, and subsequently reinforced by members of their community (Becker, 2019; Jasko et al., 2017; Jensen et al., 2018; Mills et al., 2019; Webber and Kruglanski, 2017). Even “lone wolves”, or solo actors, often interact with extremist communities online (Holt et al., 2019; Kaplan et al., 2014; Post, 2015). As such, radicalization may spread through a social contagion process, in which extremist ideologies behave like complex contagions that require multiple exposures for adoption (Guilbeault et al., 2018), which has been observed for political movements more broadly (González-Bailón et al., 2011). Previous research suggests that extremist propaganda (Ferrara, 2017), hate crimes (Braun, 2011; Braun and Koopmans, 2010), intergroup conflict (Buhaug and Gleditsch, 2008; Gelfand et al., 2012), and terrorism (Cherif et al., 2009; LaFree et al., 2012; Midlarsky et al., 1980; White et al., 2016) exhibit similar dynamics.
The environmental factors favoring radicalization, referred to here as endemic factors, include variables like poverty rate that may influence an individual’s risk of adoption in particular regions. As such, endemic factors have the potential to enhance or constrain the spread of contagions through populations across geographic space. Although significant research has been done on how endemic factors predict radicalization (and resulting violence) (Goetz et al., 2012; LaFree and Bersani, 2014; McVeigh, 2004; Medina et al., 2018; Piazza, 2017), few studies have investigated how these factors interact with contagion processes. The aim of this study is to determine whether patterns of far-right radicalization in the United States are consistent with a contagion process, and to assess the influence of critical endemic factors. After controlling for population density, I assessed the following endemic factors that have been implicated in previous research on radicalization, extremism, and mass shootings: poverty rate (Durso and Jacobs, 2013; Gale et al., 2002; Kwon and Cabrera, 2019b; Lin et al., 2018; Medina et al., 2018; Piazza, 2017; Suttmoeller et al., 2015, 2016, 2018), unemployment rate (Espiritu, 2004; Gale et al., 2002; Goetz et al., 2012; Green et al., 1998; Jefferson and Pryor, 1999; Majumder, 2017; Pah et al., 2017; Piazza, 2017), income inequality (Goetz et al., 2012; Kwon and Cabrera, 2017, 2019a, b; Majumder, 2017; McVeigh, 2004; McVeigh and Cunningham, 2012), education levels (Durso and Jacobs, 2013; Espiritu, 2004; Florida, 2011; Gladfelter et al., 2017; Kwon and Cabrera, 2017, 2019a; McVeigh et al., 2014), non-white population size (Gladfelter et al., 2017; LaFree and Bersani, 2014; McVeigh, 2004; Medina et al., 2018), violent crime rate (Gladfelter et al., 2017; McVeigh and Cunningham, 2012; Sweeney and Perliger, 2018), gun ownership (Anisin, 2018; Lin et al., 2018; Pah et al., 2017; Reeping et al., 2019), hate groups per capita (Adamczyk et al., 2014), and Republican voting (McVeigh et al., 2014; Medina et al., 2018). Furthermore, I aim to determine whether individual-level variables, such as social media use, enhance the spread of far-right radicalization over space and time. Social media platforms increasingly appear to play a role in radicalization, both as formal recruitment tools (Aly et al., 2017; Awan, 2017, Bertram, 2016; Wu, 2015) and spaces for extremist communities to interact (Amble, 2012; Dean et al., 2012; Pauwels et al., 2014; Winter, 2019). If social media platforms augment physical organizing (Bowman-Grieve, 2009; Holt et al., 2016), then they may also enhance the spread of radicalization.
Although social media platforms relax geographic constraints on communication, evidence suggests that social media networks still exhibit spatial clustering. For example, the majority of an individual’s Facebook friends live within 100 miles of them (Bailey et al., 2018), the probability of information diffusion on social media decays with increasing distance (Liu et al., 2018), and online echo chambers map onto particular locations (Bastos et al., 2018). Since complex contagions require reinforcement, and the majority of online friendship ties are within a close radius, the diffusion of extremist ideologies online should still exhibit some level of geographic bias. This idea is supported by evidence that social media enhances physical organizing among extremists (Bastug et al., 2018; Gill et al., 2017; von Behr et al., 2013), and anecdotes of “self-radicalized” individuals using social media to contact other extremists in their area (Holt et al., 2019).
In order to model the spread of far-right radicalization I used a two-component spatio-temporal intensity (twinstim) model (Meyer et al., 2017), an epidemiological method that treats events in space and time as resulting from self-exciting point processes (Reinhart, 2018). In this framework, future events depend on the history of past events within a certain geographic range. Event probabilities are determined by a conditional intensity function, which is separated into endemic and epidemic components. This allows researchers to assess the combined effects of both spatio-temporal covariates and epidemic predictors. Epidemic, in this framework, refers to any level of contagion effect and does not necessarily imply uncontrollable spread. With a couple of notable exceptions (Clark and Dixon, 2018; Zammit-Mangion et al., 2012), previous applications of self-exciting point process models in terrorism and mass shooting research have not simultaneously modeled diffusion over both time and space (Collins et al., 2020; Garcia-Bernardo et al., 2015; Johnson and Braithwaite, 2017; Lewis et al., 2012; Porter and White, 2010; Tench et al., 2016; Towers et al., 2015; White et al., 2013).
The radicalization events in this study, which correspond to where and when a radicalized individual’s extremist activity or plot was exposed, came from the Profiles of Individual Radicalization in the United States (PIRUS), an anonymized database compiled by the National Consortium for the Study of Terrorism and Responses to Terrorism (START) (National Consortium for the Study of Terrorism and Responses to Terrorism (START), University of Maryland, 2017). PIRUS is compiled from sources in the public record, and only includes individuals radicalized in the United States who were either arrested, indicted, or killed as a result of ideologically-motivated crimes, or were directly associated with a violent extremist organization. I chose to use PIRUS instead of the Terrorism and Extremist Violence in the United States (TEVUS) database because events in PIRUS are disambiguated by individual and include social variables that may influence the diffusion process.
A contagion effect in this modeling framework could result from one of two forces. The first is a copy-cat effect, in which individuals copy behaviors observed directly or in the media. Although this effect has been proposed in terrorism and mass shooting research in the past (Nacos, 2009; Towers et al., 2015), it seems to be a more plausible contagion mechanism for specific methods of violence (Helfgott, 2015) (e.g., suicide bombings (Tominaga, 2018)) rather than radicalization more broadly. The second is linkage triggered by activism and organizing, or ideologically-charged events (e.g., elections, demonstrations, policies), in that region. To differentiate between these two forces, I included two sets of epidemic predictors in the modeling. The first two event-level variables, plot success and anticipated fatalities, might be expected to increase epidemic probability if a copy-cat effect is present. This is because successful large-scale events are probably more contagious due to increased media coverage (Towers et al., 2015). Alternatively, the two individual-level variables, group membership and social media use, might be expected to increase epidemic probability if activism and organizing drive the linkage between events.
Methods
Data collection
All individual-level data came from PIRUS. Only individuals with far-right ideology who were exposed during or after 2005 (the earliest year with social media data) with location data at the city-level or lower (n = 416; F: 6.0%, M: 94.0%) were included (see Figs. 1 and 2). For each individual, the date and location of their exposure (usually when their activity/plot occurred), whether their plot was successful (34.9%), the anticipated fatalities of their plot (0: 69.5%, 1–20: 26.0%, >20:2.6%, >100: 1.9%), whether they were a member of a formal or informal group of extremists (58.4%), and whether social media played a role in their radicalization (31.2%), were included. Unknown or missing values for each predictor (plot success: 0.5%, anticipated fatalities: 13.5%, group membership: 0%, social media: 54.8%) were coded as 0. To ensure that the coding procedure for missing predictor values did not introduce bias, I checked whether the results of the full model were consistent after multiple imputation with chained equations and random forest machine learning (see Table S1). The location of each exposure was geocoded from the nearest city or town using the R package ggmap (Kahle and Wickham, 2013). Since domestic terrorists tend to commit acts in their local area (Klein et al., 2017; Marchment et al., 2018; Smith et al., 2008), I assumed that exposure locations reflect where individuals were radicalized.
State-level gun ownership was estimated using a proxy measure based on suicide rates and hunting licenses (Seigel et al., 2014). Using data from 2001, 2002, and 2004 (the only three years for which state-level gun ownership data is available), Seigel et al. found that the following proxy correlates with gun ownership with an R2 of 0.95:
$$\left(0.62\cdot \frac{{\mathrm{FS}}}{{\mathrm{S}}}\right)+(0.88\cdot {\mathrm{HL}})-0.0448$$
(1)
where FS/S is the proportion of suicides that involve firearms (from the Centers for Disease Control and Prevention, or CDC), and HL is hunting licenses per capita (from the United States Fish and Wildlife Service) (Seigel et al., 2014). Missing suicide rates (five years for DC, two years for Rhode Island) were replaced with the mean values for that state. State-level hate group data was collected from the Southern Poverty Law Center, while violent crime data was collected from the Federal Bureau of Investigation’s Uniform Crime Reporting Program.
County-level demographic data was collected from the US Census using the R package censusapi (Recht, 2019). This included population density, poverty rate, Gini index of income inequality, percentage of the population that is non-white, percentage of the population that has at least a high-school diploma, and unemployment rate. County-level income, race, education, and unemployment data is only available after 2009, so the 2010 data was used for 2005–2009. County-level presidential election voting records were collected from the Massachusetts Institute of Technology Election Lab, and non-election years were assigned the data from the most recent election year.
Geographic data was collected from the US Census using the R package tigris (Walker, 2019).
Model specification
Twinstim modeling was conducted using the R package surveillance (Meyer et al., 2017). To convert the data to a continuous spatio-temporal point process, all tied locations and dates were shifted in a random direction up to half of the minimum spatial and temporal distance between events (1.52 km and 0.5 days, respectively) (Meyer and Held, 2014).
Step functions were used to model both spatial and temporal interactions. Visual inspection of the pair correlation function for the point pattern indicates that the data is significantly clustered up to 400 km (see Supplementary Fig. 1). As such, the spatial step function was split into four 100 km intervals with 400 km as the maximum interaction radius (Nightingale et al., 2015). The temporal step function was split into four six-month intervals up to two years (based on the the high degree of variation in radicalization and attack planning times among domestic extremists (Bouhana et al., 2018; Silkoset, 2016; Smith and Damphousse, 2009)). I attempted the analysis with different combinations of power-law, Gaussian, and Student spatial functions, and exponential temporal functions, but these variations converged to unrealistically steep spatial and temporal interaction functions that approached zero around two km and two days, and appeared to be significantly influenced by the tie-breaking procedure (Meyer and Held, 2014).
Population density (county-level) was log-transformed and used as an offset endemic term. A centered time trend was also included to determine whether the strength of the endemic component has shifted over time. Poverty rate (county-level), Gini index of income inequality (county-level), gun ownership (state-level), percentage of the population that is non-white (county-level), percentage of the population that has at least a high-school diploma (county-level), unemployment rate (county-level), percentage of voters that vote Republican in presidential elections (county-level), violent crime rate per thousand residents (state-level), and number of hate groups per million residents (state-level) were included as dynamic endemic predictors that change annually. Plot success, anticipated fatalities, group membership, and social media radicalization were included as epidemic predictors.
All possible models with all possible combinations of predictors were run and ranked by Akaike’s Information Criterion (AIC) (Burnham and Anderson, 2002). The best fitting model with the lowest AIC was used to assess the effects of each variable on event probability. Rate ratios were calculated by applying exponential transformation to the model estimates.
Permutation test
To determine whether the spatio-temporal interaction of the epidemic component was statistically significant, I used the Monte Carlo permutation approach developed by Meyer et al. (Meyer et al., 2016). Using this approach, a twinstim model with all endemic predictors from the best fitting model and no epidemic predictors was compared to 1000 permuted null models with randomly shuffled event times. For each permutation I estimated the reproduction number (R0), or the expected number of future events that an event triggers on average, which represents “infectivity”. A p-value was calculated by comparing the observed R0 with the null distribution of the subset of permutations that converged.
For additional support, I also ran a likelihood ratio test and a standard Knox test of spatio-temporal clustering. The Knox test was conducted with spatial and temporal radii of 100 km and six months (the upper bounds of the first steps in the step functions), respectively (Knox and Bartlett, 1964).
Simulations
To further assess the quality of the model, I conducted simulations from the cumulative intensity function using Ogata’s modified thinning algorithm according to Meyer et al. (2012). Using the parameters of the best fitting model, I conducted 1,000 simulations of the last six months of the study period and compared the results to the observed data.
Results
The results of the best fitting model (ΔAIC < 2), which included seven endemic and two epidemic predictor variables, are shown in Table 1. Firstly, there is a statistically significant time trend whereby the endemic rate decreases by 4.6% each year, indicating that the strength of the epidemic component has increased over time. There appears to be a baseline increase in the endemic component between 2008-2012 which likely corresponds to the financial crisis (Funke et al., 2016), as well as a significant spike in the epidemic component around 2016 which likely corresponds to the presidential election (Giani and Meón, 2019; Rushin and Edwards, 2018) (Fig. 3). There are also significant positive effects of poverty rates (p < 0.01) and the presence of hate groups (p < 0.0001) on radicalization probability. Interestingly, the percentage of voters that vote Republican in presidential elections (p < 0.0001), the percentage of the population that is non-white (p < 0.05), and unemployment rates (p < 0.0001) appear to have significant negative effects on radicalization probability. Gun ownership, education level, and violent crime all have no significant effect on radicalization probability. When Republican voting was replaced with the absolute percent difference between Republican and Democratic voting, a proxy measure for the competitiveness of elections, it was no longer significant. A variance inflation factor test identified no multicollinearity problems among the time-averaged endemic predictors (VIF < 3) (Zuur et al., 2010).
Total intensity can be interpreted as the proportion of radicalization probability that is explained by the endemic and epidemic components.
Both group membership and radicalization via social media have strong and significant positive effects on epidemic probability. Exposures of individuals who belong to formal or informal extremist groups are over four times more likely to be followed by future exposures in close spatial or temporal proximity (p < 0.01). Similarly, exposures of individuals radicalized on social media are almost three times as likely to be followed by future exposures (p < 0.01). Anticipated fatalities and plot success did not appear in the best fitting model. Estimates of the decaying spatial and temporal interaction functions, as well as model diagnostics, can be seen in Supplementary Figs. 2 and 3, respectively. A variance inflation factor test identified no multicollinearity problems among the epidemic predictors (VIF < 3) (Zuur et al., 2010).
Based on the permutation test, the observed R0 (0.31) is significantly higher than the null distribution of the converged permutations (Nconv = 739, p < 0.01) (Fig. 4). This indicates that the spatio-temporal interaction in the epidemic model is significant. Both the likelihood ratio test of the epidemic against the endemic model (p < 0.0001) and the Knox test (p < 0.0001) support this result.
The grey bars show the null distribution of R0 from the 739 permutations that converged, whereas the red dashed line shows the observed R0 (0.31) calculated from the twinstim model.
The results of the simulations can be seen in Figs. 5 and 6. On average the simulations neatly match the observed cumulative number of exposures between June 2017 and January 2018 (Fig. 5), indicating that the model accurately captures the temporal dynamics in the data. Similarly, the model appears to do a good job of capturing the spatial dynamics in the data, although it is clearly weighted towards high population density areas (Fig. 6).
The color gradient, ranging from blue (low) to yellow (high), represents a Gaussian kernel density for the results of 1000 simulations with a bandwidth of 200 km. The contour lines segment the kernel density into 10 levels.
Discussion
By applying novel epidemiological methods to data on 416 extremists exposed between 2005 and 2017, this study provides evidence that patterns of far-right radicalization in the United States are consistent with a contagion process. Firstly, the estimated reproduction number is significantly higher than those from simulated null models, indicating that endemic causes alone are not sufficient to explain the spatio-temporal clustering observed in the data. The reproduction number for radicalization (R0 = 0.31) is also lower than one, suggesting that extremist ideologies behave like complex contagions that require reinforcement for transmission. Fortunately, this means that extremist ideologies are unlikely to spread uncontrollably through populations like seasonal influenza (R0 = 1.28) (Biggerstaff et al., 2014), but outbreaks can occur under the right endemic and epidemic conditions. For example, regions with higher rates of poverty and hate group activity are more likely to experience far-right extremism, whereas regions with a larger non-white population, more Republican voting, and higher rates of unemployment are less likely to experience far-right extremism. Most importantly, radicalizations involving extremist groups or social media significantly increase the epidemic probability of future radicalizations in the same location. This suggests that clusters of radicalizations in space and time are driven by activism and organizing rather than a copy-cat effect.
The fact that group membership significantly increases the epidemic strength of events, and the presence of hate groups significantly increases radicalization probability, suggests that local organizing remains a potent recruitment tool of the far-right movement. This idea is reflected in recent increases in rallies across the country, such as “Unite the Right” in Charlottesville, VA in August of 2017, that have been attended by regional chapters of white nationalist and militia organizations. It also suggests that concerns about typological “lone wolves” radicalized over social media should not overshadow the persistent and expanding far-right movement in the United States. Only 10.8% of people in this study were radicalized on social media independently of an extremist group, indicating that solo actors are still the minority in the far-right movement. That being said, solo actors radicalized on social media, such as Omar Mateen (Pulse nightclub shooting in 2016) and Dylann Roof (Charleston church shooting in 2015) (Holt et al., 2019), are typically deadlier than group members in the United States (Phillips, 2017), and should thus be the subject of much future research.
Radicalization on social media also significantly increases the epidemic strength of events, indicating that social media platforms augment physical organizing and that the diffusion of extremist ideologies online is likely geographically biased. The increasing role of social media in far-right extremism and radicalization is well established (Costello and Hawdon, 2018; Holt et al., 2019; Lowe, 2019; Ottoni et al., 2018; Winter, 2019). Social media platforms like Twitter provide extremist communities with low cost access to large audiences that might not otherwise engage with far-right content (Bertram, 2016; Wu, 2015). For example, one report found that only 44% of people who follow high-profile white nationalists on Twitter overtly express similar ideologies (Berger and Strathearn, 2013). As mainstream platforms clamp down on hate speech, extremist users have just shifted their traffic to alternative sites such as 8chan and Gab (Blackbourn et al., 2019; Hodge and Hallgrimsdottir, 2019). Given the centrality of social media in far-right organizing, future research should explore how counter-narratives (van Eerten et al., 2017; Voogt, 2017) and other strategies could be used to fight the spread of extremist ideologies online.
The results indicate that county-level poverty rates increase the probability of far-right radicalization. While there is little to no evidence that poverty predicts extremism at the state-level (Durso and Jacobs, 2013; Gale et al., 2002; Lin et al., 2018; Piazza, 2017), studies at the county-level have found that poverty predicts both mass shooting rate (Kwon and Cabrera, 2019b) and hate groups (presence (Medina et al., 2018) not longevity (Suttmoeller et al., 2015, 2016, 2018)). This discrepancy between geographic resolutions indicates that using state-level poverty data obscures local variation. The results of this study also reveal a negative effect of unemployment rate on radicalization, adding to the remarkably contradictory evidence for links between unemployment and extremism in the United States (Espiritu, 2004; Gale et al., 2002; Goetz et al., 2012; Green et al., 1998, Jefferson and Pryor, 1999; Majumder, 2017; Piazza, 2017). Although this result appears to be counter-intuitive, I hypothesize that poverty and unemployment may interact in driving radicalization. For example, individuals from regions where jobs are plentiful but poverty remains high may be the most disillusioned and susceptible to extremist ideologies. Interestingly, income inequality did not appear in the best fitting model, and had no significant effect when included. This suggests that overall deprivation, as measured by poverty rate, is more important in driving radicalization than inequality. Previous studies that have found a positive impact of income inequality on hate groups or crime either used state-level data (Majumder, 2017), did not account for poverty rate (Goetz et al., 2012; McVeigh, 2004), or combined income inequality with poverty rate into a single index (McVeigh and Cunningham, 2012). Interestingly, both unemployment (Pah et al., 2017) and income inequality (Kwon and Cabrera, 2017, 2019a, b) appear to be strong predictors of mass shootings. Although this seems paradoxical, the majority of mass shootings are not ideologically driven (Capellan, 2015), so the socioeconomic drivers may be different than for far-right radicalization.
Violent crime appears to have no influence on radicalization. Although one study of the Ku Klux Klan found that high levels of far-right activity can increase homicide rates in the long-term (McVeigh and Cunningham, 2012), there is little evidence that violent crime rates drive increases in extremist violence or radicalization (Sweeney and Perliger, 2018). Hate crime is only very weakly correlated with violent crime (Gladfelter et al., 2017), and extremist violence is even more rare (LaFree and Dugan, 2009), so they are likely driven by different factors.
Previous studies have found strong evidence for a negative relationship between education and hate crime rates (Espiritu, 2004; Gladfelter et al., 2017), a positive relationship between education and mass shooting rates (Kwon and Cabrera, 2017, 2019a), and no evidence for a relationship between education and hate group organizing (Durso and Jacobs, 2013; Florida, 2011; McVeigh et al., 2014). The results of this study are consistent with the latter category, which makes sense given that the majority of the plots in the dataset were non-violent.
The negative effect of Republican voting on event probability could be because individuals on the far-right of the political spectrum who live in counties with more Democratic voters may feel more partisan hostility (Miller and Conover, 2015). Interestingly, this effect does not appear to be the result of more competitive elections (Suttmoeller et al., 2015), as the absolute difference between Republican and Democratic voting did not significantly influence event probability. Alternatively, the negative effect of Republican voting may be due to the fact that many of the rural counties that lean heavily Republican have low population densities and no recent history of extremist violence. A previous study that found mixed evidence for a positive influence of Republican voting on the presence of hate groups excluded counties without hate groups from the modeling, which may have eliminated this skew effect (Medina et al., 2018).
The fact that the percentage of the population that is non-white negatively predicts far-right extremist violence is consistent with the intergroup contact hypothesis, which suggests that prolonged contact between racial groups reduces conflict under certain conditions (Allport, 1954). Although other researchers have suggested that population heterogeneity increases far-right radicalization (McVeigh, 2004), the only study to find evidence of this in the United States did not explicitly account for population density (LaFree and Bersani, 2014). Other studies controlling for population density have found that both anti-black hate crimes and hate groups appear to be more common in white dominated, racially homogeneous areas (Gladfelter et al., 2017; Medina et al., 2018). Despite mixed evidence for the intergroup contact hypothesis, it is widely accepted that community diversity and tolerance is key to fighting radicalization and extremist violence globally (Ellis and Abdi, 2017; Ercan, 2017; Gunaratna et al., 2013; Hoffman et al., 2018; Southern Poverty Law Center, 2017; United Nations Development Programme, 2016).
Gun ownership does not predict radicalization in this model, which is unsurprising since only 30.5% of people in this study planned on committing fatal attacks but interesting given the centrality of gun control in debates following mass shootings in the United States (Joslyn and Haider-Markel, 2017; Luca et al., 2020; Pierre, 2019). Despite strong evidence that gun ownership is linked to mass shooting rates at the national-level (Reeping et al., 2019), evidence for same pattern at the state-level remains mixed. Previous studies have found that it either positively predicts mass shootings overall (Reeping et al., 2019), when combined with particular gun control laws (Anisin, 2018), or not at all (Lin et al., 2018; Pah et al., 2017). Unfortunately, CDC funding for research on gun ownership was restricted by Congress in 1996 after lobbying by the National Rifle Association, so potential links between extremist violence and gun ownership remain understudied (DeFoster and Swalve, 2018; Lemieux, 2014; Morall, 2018; Winker et al., 2016).
Several limitations of this study should be highlighted. Firstly, the PIRUS database only represents a subset of radicalized individuals in the United States. The creators of the database used random sampling to maximize its representativeness over different time periods, but there remains a possibility of spatial or temporal bias in the original data due to underreporting by victims and law enforcement effort (DiIulio, 1996). Instances of hate crime are notoriously underreported relative to other forms of crime (Pezzella et al., 2019), because victims often fear retaliation or mistrust the police (Pezzella, 2017; Weiss et al., 2016; Wong and Christmann, 2016). There is also a great deal of variation in hate crime training among police departments, and the personal beliefs of individual officers can influence whether or not instances are reported (Boyd et al., 1996; Pezzella, 2017). Both of these factors are likely to be more pronounced in areas with legacies of far-right extremist violence, and historical crossover between far-right groups and the police (Barnes, 1996; Johnson, 2019; Rowe, 1976). In addition, the geographic locations of events are only geocoded to the city-level, potentially enhancing the spatial clustering of the data. Furthermore, social media data were missing for a significant number of individuals (54.8%). The significance level of the estimate for social media usage is extremely low and robust to imputation, indicating that it likely reflects a real effect, but researchers should exercise caution when interpreting this result (Safer-Lichtenstein et al., 2017). Lastly, the spatial resolution of three of the endemic predictors was limited to the state-level, which may have flattened some important local variation. One of these variables, gun ownership, was also a proxy measure. Policymakers should release historical restrictions on research funding for gun violence and hate crime research to improve data resolution for future studies.
In conclusion, far-right radicalization in the United States appears to spread through populations like a complex contagion. Both social media usage and group membership enhance the contagion process, indicating that online and physical organizing remain primary recruitment tools of the far-right movement. In addition, far-right radicalization is more likely in Democrat-majority regions with high poverty and low unemployment, fewer non-white people, and more hate group activity. While the federal government has acknowledged the threat of far-right extremism (The Department of Homeland Security, 2019), funding for organizations researching or fighting the movement has decreased in recent years (O’Toole, 2019). Based on the results of this study, I recommend that policymakers reconsider their funding priorities to address the expanding far-right extremist movement in the United States. Future research should investigate how specific interventions, such as online counter-narratives to battle propaganda, may be effectively implemented to mitigate the spread of extremist ideology.
Similar content being viewed by others
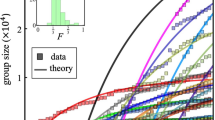
N. Velásquez, P. Manrique, … N. F. Johnson

Marta Martins
Koen van der Zwet, Ana I. Barros, … Peter M. A. Sloot
Data availability
All data used in the study are available online either publicly or upon request from PIRUS. The R code used in the study is available on Harvard Dataverse: https://doi.org/10.7910/DVN/WPYCKJ
References
Adamczyk A, Gruenewald J, Chermak SM, Freilich JD (2014) The relationship between hate groups and far-right ideological violence. J Contemp Crim Justice 30(3):310–332
Allam H (2019) ‘We were blindsided’: families of extremists form group to fight hate. National Public Radio (12)
Allport G (1954) The nature of prejudice. Addison-Wesley, Cambridge
Aly A, Macdonald S, Jarvis L, TM Chen (2017) Introduction to the special issue: terrorist online propaganda and radicalization. Stud Confl Terror 40(1):1–9
Amble JC (2012) Combating terrorism in the new media environment. Stud Confl Terror 35(5):339–353
Anisin A (2018) A configurational analysis of 44 US mass shootings: 1975-2015. Int J Comparat Appl Criminal Justice 42(1):55–73
Awan I (2017) Cyber-extremism: Isis and the power of social media. Society 54(2):138–149
Bailey M, Cao R, Kuchler T, Stroebel J, Wong A (2018) Social connectedness: measurement, determinants, and effects. J Econ Perspect 32(3):259–280
Barnes RD (1996) Blue by day and white by (k)night: regulating the political affiliations of law enforcement and military personnel. Iowa Law Rev 81:1079
Bastos M, Mercea D, Baronchelli A (2018) The geographic embedding of online echo chambers: evidence from the Brexit campaign. PLoS ONE 13(11):1–16
Bastug M, Douai A, Akca D (2018) Exploring the "demand side” of online radicalization: evidence from the Canadian context. Stud Confl Terror. https://doi.org/10.1080/1057610X.2018.1494409
Becker MH (2019) When extremists become violent: examining the association between social control, social learning, and engagement in violent extremism. Stud Confl Terror. https://doi.org/10.1080/1057610X.2019.1626093
Berger JM, Strathearn B (2013) Who matters online: measuring influence, evaluating content and countering violent extremism in online social networks. The International Centre for the Study of Radicalisation and Political Violence. https://bit.ly/35lvqby
Bertram L (2016) Terrorism, the Internet, and the Social Media Advantage: Exploring how terrorist organizations exploit aspects of the internet, social media and how these same platforms could be used to counter-violent extremism. J Deradical 7:225–252
Biggerstaff M, Cauchemez S, Reed C, Gambhir M, Finelli L (2014) Estimates of the reproduction number for seasonal, pandemic, and zoonotic influenza: a systematic review of the literature BMC Infect Dis 14:480
Blackbourn J, McGarrity N, Roach K (2019) Understanding and responding to right wing terrorism. J Polic Intell Count Terror 14(3):183–190
Bonn T (2019) Former extremists call for violent extremism to be treated as public health issue. The Hill (9)
Bouhana N, Corner E, Gill P, Schuurman B (2018) Background and preparatory behaviours of right-wing extremist lone actors: a comparative study. Perspect Terror 12(6):150–163
Bowman-Grieve L (2009) Exploring stormfront: a virtual community of the radical right. Stud Confl Terror 32(11):989–1007
Boyd EA, Berk RA, Hamner KM (1996) "Motivated by hatred or prejudice”: categorization of hate-motivated crimes in two police divisions. Law Soc Rev 30(4):819–850
Braun R (2011) The diffusion of racist violence in the Netherlands: discourse and distance. J Peace Res 48(6):753–766
Braun R, Koopmans R (2010) The diffusion of ethnic violence in Germany: the role of social similarity. Eur Sociol Rev 26(1):111–123
Buhaug H, Gleditsch KS (2008) Contagion or confusion? why conflicts cluster in space. Int Stud Q 52(2):215–233
Burnham KP, Anderson DR (2002) Model selection and multimodel inference: a practical information-theoretic approach. Springer, New York
Capellan JA (2015) Lone wolf terrorist or deranged shooter? a study of ideological active shooter events in the United States, 1970-2014. Stud Confl Terror 38(6):395–413
Cherif A, Yoshioka H, Ni W, Bose P (2009) Terrorism: mechanisms of radicalization processes, control of contagion and counter-terrorist measures. Preprint at arXiv: 0910.5272
Clark NJ, Dixon PM (2018) Modeling and estimation for self-exciting spatio-temporal models of terrorist activity. Ann Appl Stat 12(1):633–653
Collins B, Hoang DT, Yoon HJ, Nguyen NT, Hwang D (2020) A survey on forecasting models for preventing terrorism. In: Advanced computational methods for knowledge engineering. Springer, Cham, pp 323–334
Costello M, J Hawdon (2018) Who are the online extremists among us? sociodemographic characteristics, social networking, and online experiences of those who produce online hate materials. Violence Gender 5(1):55–60
Davey J, Ebner J (2019) ‘The great replacement’: the violent consequences of mainstreamed extremism. Institute for Strategic Dialogue. https://bit.ly/2yXdl7h
Dean G, Bell P, Newman J (2012) The dark side of social media: review of online terrorism. Pak J Criminol 3(3):107–126
DeFoster R, Swalve N (2018) Guns, culture or mental health? framing mass shootings as a public health crisis. Health Commun 33(10):1211–1222
DiIulio JJ (1996) Help wanted: economists, crime and public policy. J Econ Perspect 10(1):3–24
Durso RM, Jacobs D (2013) The determinants of the number of white supremacist groups: a pooled time-series analysis. Soc Probl 60(1):128–144
Ellis BH, Abdi S (2017) Building community resilience to violent extremism through genuine partnerships. Am Psychol 72(3):289–300
Ercan SA (2017) Engaging with extremism in a multicultural society: a deliberative democratic approach. J Peacebuild Dev 12(2):9–21
Espiritu A (2004) Racial diversity and hate crime incidents. Soc Sci J 41(2):197–208
Ferrara E (2017) Contagion dynamics of extremist propaganda in social networks. Inf Sci 418-419:1–12
Florida R (2011) The geography of hate. The Atlantic (5)
Funke M, Schularick M, Trebesch C (2016) Going to extremes: politics after financial crises, 1870-2014. Eur Econ Rev 88(2011):227–260
Gale LR, Heath WC, Ressler RW (2002) An economic analysis of hate crime. East Econ J 28(2):203–216
Garcia-Bernardo J, Qi H, Shultz JM, Cohen AM, Johnson NF, Dodds PS (2015) Social media affects the timing, location, and severity of school shootings. Preprint at arXiv: 1506.06305
Gelfand M, Shteynberg G, Lee T, Lun J, Lyons S, Bell C, Chiao JY, Bruss CB, Dabbagh MA, Aycan Z, Abdel-Latif AH, Dagher M, Khashan H, Soomro N (2012) The cultural contagion of conflict. Philos Trans R Soc B 367(1589):692–703
Giani M, Meón PG (2019) Global racist contagion following Donald Trump’s election. Br J Polit Sci. https://doi.org/10.1017/S0007123419000449
Gill P, Corner E, Conway M, Thornton A, Bloom M, Horgan J (2017) Terrorist use of the internet by the numbers: quantifying behaviors, patterns, and processes. Criminol Public Policy 16(1):99–117
Gladfelter AS, Lantz B, Ruback RB (2017) The complexity of hate crime and bias activity: variation across contexts and types of bias. Justice Q 34(1):55–83
Goetz SJ, Rupasingha A, Loveridge S (2012) Social capital, religion, Wal-Mart, and hate groups in America. Soc Sci Q 93(2):379–393
González-Bailón S, Borge-Holthoefer J, Rivero A, Moreno Y (2011) The dynamics of protest recruitment through an online network. Sci Rep 1(197):1–7
Green DP, Glaser J, Rich A (1998) From lynching to gay bashing: the elusive connection between economic conditions and hate crime. J Pers Soc Psychol 75(1):82–92
Guilbeault D, Becker J, Centola D (2018) Complex contagions: a decade in review. In: Complex spreading phenomena in social systems. Springer, Cham, pp 3–25
Gunaratna R, Jerard J, Nasir SM (2013) Countering extremism: building social resilience through community engagement. Imperial College Press, London
Helfgott JG (2015) Criminal behavior and the copycat effect: literature review and theoretical framework for empirical investigation. Aggress Violent Behav 22:46–64
Hodge E, Hallgrimsdottir H (2019) Networks of hate: the alt-right, “troll culture”, and the cultural geography of social movement spaces online. J Borderl Stud https://doi.org/10.1080/08865655.2019.1571935
Hoffman AJ, Alamilla S, Liang B (2018) The role of community development in reducing extremism and ethnic conflict. Palgrave MacMillan, Cham
Holt TJ, Freilich JD, Chermak SM (2016) Internet-based radicalization as enculturation to violent deviant subcultures. Deviant Behav 38(8):855–869
Holt TJ, Freilich JD, Chermak SM, Mills C, Silva J (2019) Loners, colleagues, or peers? assessing the social organization of radicalization. Am J Crim Justice 44(1):83–105
Jasko K, LaFree G, Kruglanski A (2017) Quest for significance and violent extremism: the case of domestic radicalization. Polit Psychol 38(5):815–831
Jefferson PN, Pryor FL (1999) On the geography of hate. Econ Lett 65(3):389–395
Jensen MA, Seate AA, James PA (2018) Radicalization to violence: a pathway approach to studying extremism. Terror Polit Violence. https://doi.org/10.1080/09546553.2018.1442330
Johnson VB (2019) KKK in the PD: white supremacist police and what to do about it. Lewis Clark Law Rev 23(1):205–261
Johnson SD, Braithwaite A (2017) Spatial and temporal analysis of terrorism and insurgency. In: The handbook of the criminology of terrorism. Wiley, Hoboken, pp 232–243
Joslyn MR, Haider-Markel DP (2017) Gun ownership and self-serving attributions for mass shooting tragedies. Soc Sci Q 98(2):429–442
Kahle D, Wickham H (2013) ggmap: spatial visualization with ggplot2. R J 5(1):144–161
Kaplan J, Lööw H, L Malkki (2014) Introduction to the special issue on lone wolf and autonomous cell terrorism. Terror Polit Violence 26(1):1–12
Klein BR, Gruenewald J, Smith BL (2017) Opportunity, group structure, temporal patterns, and successful outcomes of far-right terrorism incidents in the United States. Crime Delinq 63(10):1224–1249
Knox EG, Bartlett MS (1964) The detection of space-time interactions. J Royal Stat Soc C 13(1):25–30
Kwon R, Cabrera JF (2017) Socioeconomic factors and mass shootings in the United States. Crit Public Health 28(2):138–145
Kwon R, Cabrera JF (2019a) Income inequality and mass shootings in the United States. BMC Public Health 19:1147
Kwon R, Cabrera JF (2019b) Social integration and mass shootings in U.S. counties. J Crime Justice 42(2):121–139
LaFree G, Bersani BE (2014) County-level correlates of terrorist attacks in the United States. Criminol Public Policy 13(3):455–481
LaFree G, Dugan L (2009) Tracking global terrorism trends, 1970-2004. In: To protect and to serve: policing in an age of terrorism. Springer, New York, pp 43–80
LaFree G, Dugan L, Xie M, P Singh (2012) Spatial and temporal patterns of terrorist attacks by ETA 1970 to 2007. J Quant Criminol 28(1):7–29
Lemieux F (2014) Effect of gun culture and firearm laws on gun violence and mass shootings in the United States: a multi-level quantitative analysis. Int J Crim Justice Sci 9(1):74–93
Lewis E, Mohler G, Brantingham PJ, Bertozzi AL (2012) Self-exciting point process models of civilian deaths in Iraq. Security J 25(3):244–264
Lin PI, Fei L, Barzman D, Hossain M (2018) What have we learned from the time trend of mass shootings in the U.S.? PLoS ONE 13(10):1–13
Liu L, Chen B, Ai C, He L, Wang Y, Qiu X, Lu X (2018) The influence of geographic factors on information dissemination in mobile social networks in China: evidence from WeChat. ISPRS Int J Geoinf 7(5):1–16
Lowe D (2019) The Christchurch terrorist attack, the far-right, and social media: what can we Learn? The New Jurist (4)
Luca M, Malhotra D, Poliquin C (2020) The impact of mass shootings on gun policy. J Public Econ 181:104083
Majumder M (2017) Higher rates of hate crimes are tied to income inequality. FiveThirtyEight (1)
Marchment Z, Bouhana N, Gill P (2018) Lone actor terrorists: a residence-to-crime approach. Terror Political Violence. https://doi.org/10.1080/09546553.2018.1481050
McVeigh R (2004) Structured ignorance and organized racism in the United States. Soc Forces 82(3):895–936
McVeigh R, Cunningham D (2012) Enduring consequences of right-wing extremism: Klan mobilization and homicides in southern counties. Soc Forces 90(3):843–862
McVeigh R, Cunningham D, Farrell J (2014) Political polarization as a social movement outcome: 1960s Klan activism and its enduring impact on political realignment in southern counties, 1960 to 2000. Am Sociol Rev 79(6):1144–1171
Medina RM, Nicolosi E, Brewer S, Linke AM (2018) Geographies of organized hate in America: a regional analysis. Ann Am Assoc Geogr 108(4):1006–1021
Meyer S, Elias J, Höhle M (2012) A space-time conditional intensity model for invasive meningococcal disease occurrence. Biometrics 68(2):607–616
Meyer S, Held L (2014) Power-law models for infectious disease spread. Ann Appl Stat 8(3):1612–1639
Meyer S, Held L, Höhle M (2017) Spatio-temporal analysis of epidemic phenomena using the R package surveillance. J Stat Softw 77(11):1–55
Meyer S, Warnke I, Rössler W, Held L (2016) Model-based testing for space-time interaction using point processes: an application to psychiatric hospital admissions in an urban area. Spat Spatio-Temporal Epidemiol 17:15–25
Midlarsky MI, Crenshaw M, Yoshida F (1980) Why violence spreads: the contagion of international terrorism. Int Stud Q 24(2):262–298
Miller PR, Conover PJ (2015) Red and blue states of mind: partisan hostility and voting in the United States. Polit Res Q 68(2):225–239
Mills CE, Freilich JD, Chermak SM, Holt TJ, LaFree G (2019) Social learning and social control in the off- and online pathways to hate crime and terrorist violence. Stud Confl Terror. https://doi.org/10.1080/1057610X.2019.1585628
Misiak B, Samochowiec J, Bhui K, Schouler-Ocak M, Demunter H, Kuey L, Raballo A, Gorwood P, Frydecka D, Dom G (2019) A systematic review on the relationship between mental health, radicalization and mass violence. Eur Psychiatry 56:51–59
Morall A (2018) The science of gun policy: a critical synthesis of research evidence on the effects of gun policies in the united states. RAND Health Quart 8:1
Nacos BL (2009) Revisiting the contagion hypothesis: terrorism, news coverage, and copycat attacks. Perspect Terror 3(3):3–13
National Consortium for the Study of Terrorism and Responses to Terrorism (START), University of Maryland (2017). Profiles of Individual Radicalization in the United States (PIRUS). https://bit.ly/2yWtmu8
Nightingale GF, Laland KN, Hoppitt W, Nightingale P (2015) Bayesian spatial NBDA for diffusion data with home-base coordinates. PLoS ONE 10(7):e0130326
O’Toole M (2019) Trump officials have redirected resources from countering far-right, racism-fueled domestic terrorism. Los Angeles Times (8)
Ottoni R, Bernardina P, Cunha E, Meira W, Magno G, Almeida V (2018) Analyzing right-wing YouTube channels: hate, violence and discrimination. In: WebSci 2018 Proceedings of the 10th ACM Conference On Web Science, Amsterdam, pp 323–332
Pah AR, Hagan J, Jennings AL, Jain A, Albrecht K, Hockenberry AJ, Amaral LA (2017) Economic insecurity and the rise in gun violence at US schools. Nat Hum Behav 1(2):2–7
Pauwels L, Brion F, Schils N, Laffineur J, Verhage A, de Ruyver B, Easton M (2014) Explaining and understanding the role of exposure to new social media in violent extremism: an integrative quantitative and qualitative approach. Academia Press, Gent
Pezzella FS (2017) Hate crime statutes: a public policy and law enforcement dilemma. Springer, New York
Pezzella FS, Fetzer MD, Keller T (2019) The dark figure of hate crime underreporting. Am Behav Sci. https://doi.org/10.1177/0002764218823844
Phillips BJ (2017) Deadlier in the U.S.? on lone wolves, terrorist groups, and attack lethality. Terror Polit Violence 29(3):533–549
Piazza JA (2017) The determinants of domestic right-wing terrorism in the USA: economic grievance, societal change and political resentment. Confl Manag Peace Sci 34(1):52–80
Pierre JM (2019) The psychology of guns: risk, fear, and motivated reasoning. Pal Commun 5(1):1–7
Porter MD, White G (2010) Self-exciting hurdle models for terrorist activity. Ann Appl Stat 4(1):106–124
Post JM (2015) Terrorism and right-wing extremism: the changing face of terrorism and political violence in the 21st century: the virtual community of hatred. Int J Group Psychoth 65(2):242–271
Recht H (2019) censusapi: retrieve data from the census APIs. R package version 0.6.0
Reeping PM, Cerdá M, Kalesan B, Wiebe DJ, Galea S, Branas CC (2019) State gun laws, gun ownership, and mass shootings in the US: cross sectional time series. BMJ 364:1542
Reinhart A (2018) A review of self-exciting spatio-temporal point processes and their applications. Stat Sci 33(3):299–318
Rowe G (1976) My undercover years with the Ku Klux Klan. Bantam Books, New York
Rushin S, Edwards GS (2018) The effect of President Trump’s election on hate crimes. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3102652
Safer-Lichtenstein A, LaFree G, Loughran T (2017) Studying terrorism empirically: what we know about what we donat know. J Contemp Crim Justice 33(3):273–291
Sanir J, Nicholson A, Giammaria C (2017) Countering violent extremism through public health practice: proceedings of a workshop. In: Forum on medical and public health preparedness for disasters and emergencies. The National Academies Press, Washington, DC
Seigel M, Ross C, King C (2014) A new proxy measure for state-level gun ownership in studies of firearm injury prevention. Inj Prev 20(3):204–207
Silkoset E (2016) Lone-actor terrorists: how long does it take to plan a terrorist attack? Dissertation, University College of London
Simi P, Bubolz BF (2017) Far right terrorism in the United States. In: The handbook of the criminology of terrorism, Wiley, Hoboken. pp 297–309
Smith BL, Cothren J, Roberts P, Damphousse KR (2008) Geospatial analysis of terrorist activities: the identification of spatial and temporal patterns of preparatory behavior of international and environmental terrorists. Terrorism Research Center in Fulbright College, University of Arkansas. https://bit.ly/2SibIIc
Smith BL, Damphousse KR (2009) Patterns of precursor behaviors in the life span of a U.S. environmental terrorist group. Criminol Public Policy 8(3):475–496
Southern Poverty Law Center (2017) Ten ways to fight hate: a community resource guide. https://bit.ly/35j4TLN
Suttmoeller M, Chermak S, Freilich JD (2015) The influence of external and internal correlates on the organizational death of domestic far-right extremist groups. Stud Confl Terror 38(9):734–758
Suttmoeller MJ, Chermak SM, Freilich JD (2016) Only the bad die young: the correlates of organizational death for far-right extremist groups. Stud Confl Terror 39(6):477–499
Suttmoeller MJ, Chermak SM, Freilich JD (2018) Is more violent better? the impact of group participation in violence on group longevity for far-right extremist groups. Stud Confl Terror 41(5):365–387
Sweeney MM, Perliger A (2018) Explaining the spontaneous nature of far-right violence in the United States. Perspect Terror 12(6):52–71
Tench S, Fry H, Gill P (2016) Spatio-temporal patterns of IED usage by the Provisional Irish Republican Army. Eur J Appl Math 27(3):377–402
The Anti-Defamation League Center on Extremism (2019) Murder and extremism in the United States in 2018. https://bit.ly/2VLy5If
The Department of Homeland Security (2019) Strategic framework for countering terrorism and target violence. https://bit.ly/2xhCCsB
Tominaga Y (2018) Thereas no place like home! examining the diffusion of suicide attacks through terrorist group locations. Appl Spat Anal Policy 11(2):355–379
Towers S, Gomez-Lievano A, Khan M, Mubayi A, Castillo-Chavez C (2015) Contagion in mass killings and school shootings. PLoS ONE 10(7):e0117259
United Nations Development Programme (2016) Preventing violent extremism through promoting inclusive development, tolerance and respect for diversity. https://bit.ly/2KJzxVa
van Eerten JJ, Doosje B, Konijn E, de Graaf B, de Goede M (2017) Developing a social media response to radicalization: the role of counter-narratives in prevention of radicalization and de-radicalization. Wetenschappelijk Onderzoek-en Documentatiecentrum. https://bit.ly/2VMRkBc
von Behr I, Reding A, Edwards C, Gribbon L (2013) Radicalisation in the digital era: the use of the internet in 15 cases of terrorism and extremism. RAND Europe. https://bit.ly/37AOnIn
Voogt S (2017) Countering far-right recruitment online: CAPEas practitioner experience. J Polic Intelligence Counter Terrorism 12(1):34–46
Walker K (2019) tigris: load vensus TIGER/line shapefiles. R package version 0.8.2
Webber D, Kruglanski AW (2017) Psychological factors in radicalization: a “3 N” approach. In: The handbook of the criminology of terrorism. Wiley, Hoboken, pp 33–46
Weine S, Eisenman, D (2016) How public health can improve initiatives to counter violent extremism. National Consortium for the Study of Terrorism and Responses to Terrorism. https://bit.ly/3cVtvNm
Weiss JC, McDevitt J, Iwama JA (2016) Group work with victims of hate crimes. In: Greif GL, Knight C (ed) Group work with populations at risk, 4th edn. Oxford, New York, pp 291–311
White G, Porter MD, Mazerolle L (2013) Terrorism risk, resilience and volatility: a comparison of terrorism patterns in three southeast Asian countries. J Quant Criminol 29(2):295–320
White G, Ruggeri F, Porter MD (2016) Modelling the proliferation of terrorism via diffusion and contagion. Preprint at arXiv 1612.02527
Winker MA, Abbasi K, Rivara FP (2016) Unsafe and understudied: the US gun problem. BMJ 352:i578
Winter A (2019) Online hate: from the far-right to the ‘alt-right’ and from the margins to the mainstream. In: Online Othering. Springer, Cham, pp 39–63
Wong K, Christmann K (2016) Increasing hate crime reporting: narrowing the gap between policy aspiration, victim inclination and agency capability. Br J Commun Justice 14(3):5–23
Wu P (2015) Impossible to regulate? social media, terrorists, and the role for the U.N. Chic J Int Law 16(1):281–311
Zammit-Mangion A, Dewar M, Kadirkamanathan V, Sanguinetti G (2012) Point process modelling of the Afghan War Diary. PNAS 109(31):12414–12419
Zuur AF, Ieno EN, Elphick CS (2010) A protocol for data exploration to avoid common statistical problems. Methods Ecol Evol 1(1):3–14
Acknowledgements
I would like to thank David Lahti, Bobby Habig, and the rest of the Lahti lab for their valuable conceptual feedback.
Ethics declarations
Competing interests
The author declares no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
Applying Public Health Models and Approaches to Countering Violent Extremism


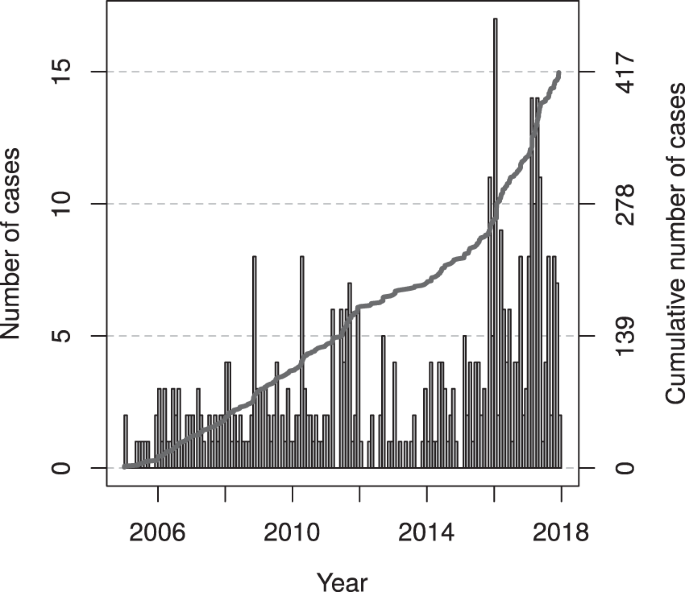
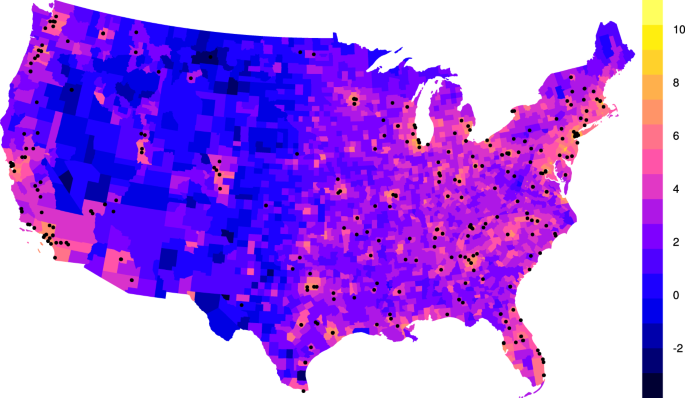
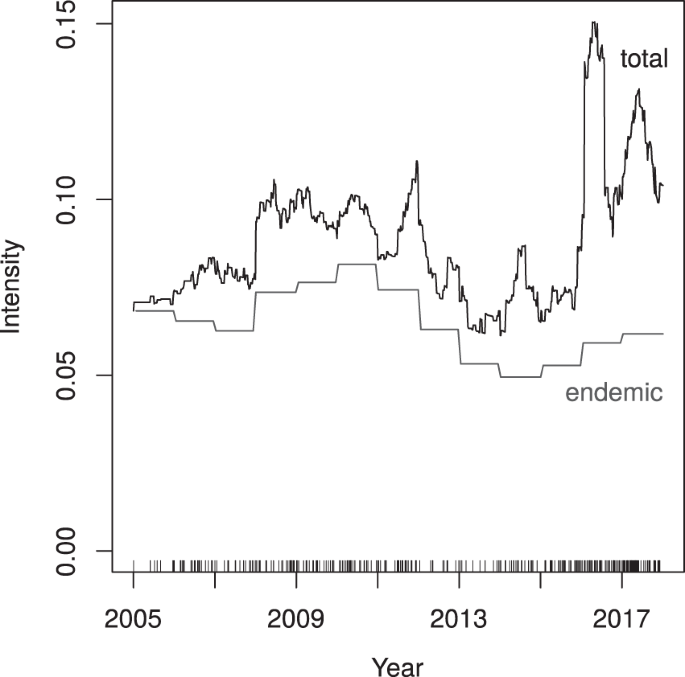
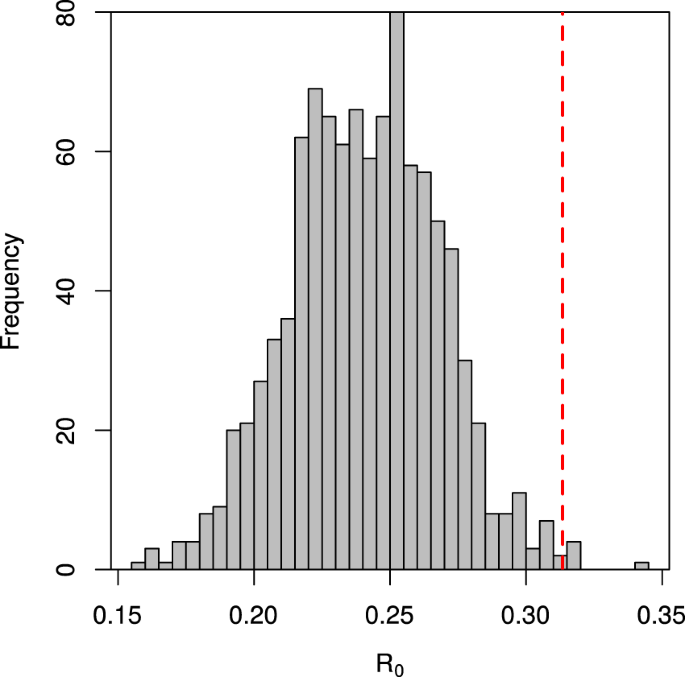
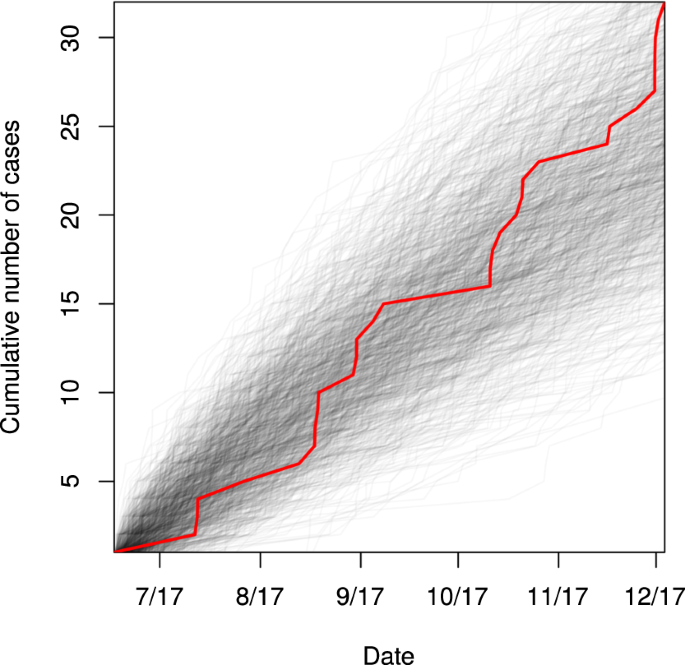
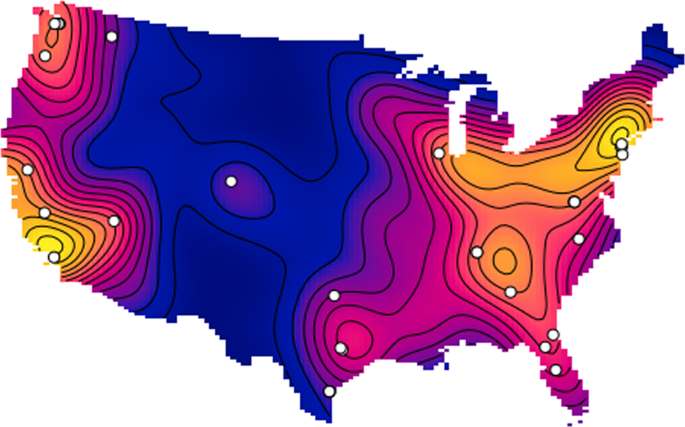







Comments
Post a Comment